Here’s a case where customer wants to create BGP over GRE tunnels between Palo Alto Firewall and Aviatrix Transit Gateways. Palo Alto have some articles but not very clear, this blog will serve as a reminder how this is done. Credit to Pranay for helping out the BGP peering part on Palo.
Continue readingCategory Archives: aws
Direct Connect to Aviatrix Transit – Option 1
This is the first of the three articles. It will be the easiest to accomplish but with following requirements, and constrains highlighted.
- Virtual Private Gateway (VGW) has to be created in the same region as the Direct Connect Private Virtual Interface (VIF).
- Each VIF is dedicated to one VGW.
- VGW is NOT attached to the VPC
- Aviatrix orchestrate Customer Gateways and VPN Connections, building 2x IPSec/BGP tunnels per Aviatrix Transit Gateway.
- Each IPSec tunnel have 1.25G throughput limit
- Private Virtual Interface support up to 100 BGP routes, BGP session will go DOWN when more routes been advertised. In layman’s term when this happens, Cloud won’t see OnPrem routes, and OnPrem won’t see Cloud routes, connectivity between Cloud and OnPrem will be LOST. You must summarize advertised routes on both ends to be lower than 100 to get around this limit.
- Between On-Premise to VGW, traffic maybe protected by MACSec, but still expose to man in the middle attack. Reference article: Securing your network connection to the cloud: MACSec vs. IPSec
Using AWS TGW Connect with Aviatrix Transit to build GRE tunnels
When customers are migrating to Aviatrix Transit from AWS TGW, we would build BGP connectivity between AWS TGW with Aviatrix Transit. In the past, we have to use IPSec, which would be limited to 1.25G per tunnel connection speed, for customer’s that doesn’t require end to end encryption during the migration, with AWS TGW Connect, now we can build GRE tunnels between AWS TGW and Aviatrix Transit.
Continue readingMulti-homed VM in different Clouds
Many enterprises venture into clouds and find the landscape of cloud networking very different from on-prem. Multi-homed devices such as routers and firewalls when deploy to the cloud also are having challenges to insert themself into traffic path, particularly due the reasons listed below. This in turn slows down the enterprises adoption speed to the cloud. Let’s take a look what some of these challenges are:
Continue readingTechTalk | Securing Cloud Egress—The Easy Way
When operating in the cloud, enterprises often struggle with how to gain control of network traffic leaving their environments in a centralized, cost-effective, and CSP-agnostic way.
In this webinar, you’ll learn how to make cloud egress architecture simple, repeatable, and automated—including how to:
- Gain visibility and control of internet-destined traffic in a cost-effective way (FQDN, subtopics distributed, centralized)
- Insert next-generation firewalls into internet-outbound traffic and deal with thousands of route entries
- Scale up and scale out your egress firewalls in an active manner and retain existing flows
- Plus, the benefits of leveraging Aviatrix FireNet and ThreatIQ, ThreatGuard, and Anomaly Detection.
Compare AWS resource configurations
So you have created your resources manually in AWS and it works fine, but when you tried to create the resource using Terraform and it just won’t work?
I’ve ran into this issue when tried to create S3 + Policy + Roles for Palo Alto bootstrap, and here below is how to resolve this, please feel free to comment if you have better methods.
Background:
I’ve followed this article and created S3 bucket, folder structure, uploaded bootstrap.xml and init-cfg.txt under config folder and it works fine. But when I tried to terraform scripts from my buddy and it just doesn’t work. There must be some delta that’s causing the issue.
It’s a very easy problem to tackle in Azure, for most resources, you can choose to export to ARM or BICEP template, which will reveal all configurations.
It isn’t as straight forward in AWS, when I’m looking at AWS CLI, aws s3 command have following subcommands
$ aws s3 ?
usage: aws [options] <command> <subcommand> [<subcommand> ..] [parameters]
To see help text, you can run:
aws help
aws <command> help
aws <command> <subcommand> help
aws: error: argument subcommand: Invalid choice, valid choices are:
ls | website
cp | mv
rm | sync
mb | rb
presignNone of them related to describe the current configuration
There is an s3api command, but it appears that you must query each subcommands, such as following huge list, what if my solution is much more complicated than just S3, then this will snowball much quicker to manage
get-bucket-accelerate-configuration
get-bucket-acl
get-bucket-analytics-configuration
get-bucket-cors
get-bucket-encryption
get-bucket-intelligent-tiering-configuration
get-bucket-inventory-configuration
get-bucket-lifecycle-configuration
get-bucket-location
get-bucket-logging
get-bucket-metrics-configuration
get-bucket-notification-configuration
get-bucket-ownership-controls
get-bucket-policy
get-bucket-policy-status
get-bucket-replication
get-bucket-request-payment
get-bucket-tagging
get-bucket-versioning
get-bucket-website
get-object
get-object-acl
get-object-attributes
get-object-legal-hold
get-object-lock-configuration
get-object-retention
get-object-tagging
get-object-torrent
get-public-access-blockThen I’ve come across AWS Config, which should track configuration of each resources
AWS Config – Getting started
- First goes to the region of the resources you want to track, and search for Config

- Click on Get started. I have selected Include global resources as there’s a need to track roles and policies and choose to create a new bucket
- Rules are meant to be auditing purpose to evaluate if your resources is following best practices, which isn’t useful for my situation, so I didn’t select anything

- Finally review and confirm

AWS Config – comparing resources
Going to AWS Config -> Dashboard, it nicely listed all discovered resources by category. Since we need to compare the S3 configuration, then I’ve clicked on S3 Bucket
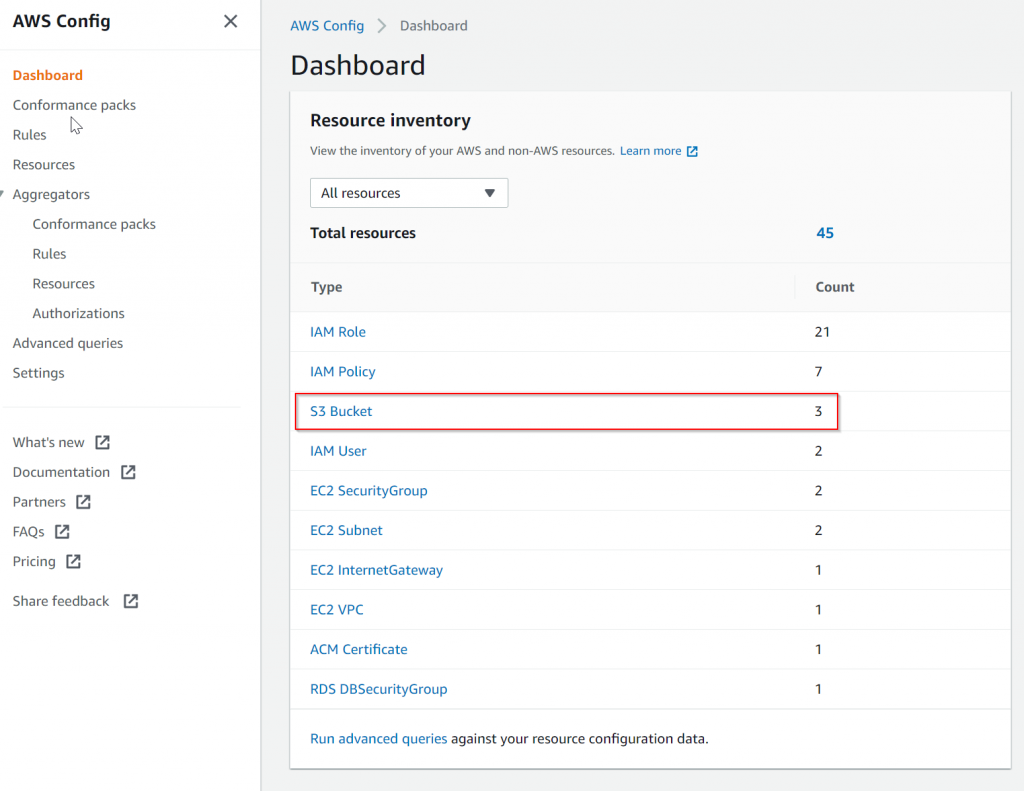
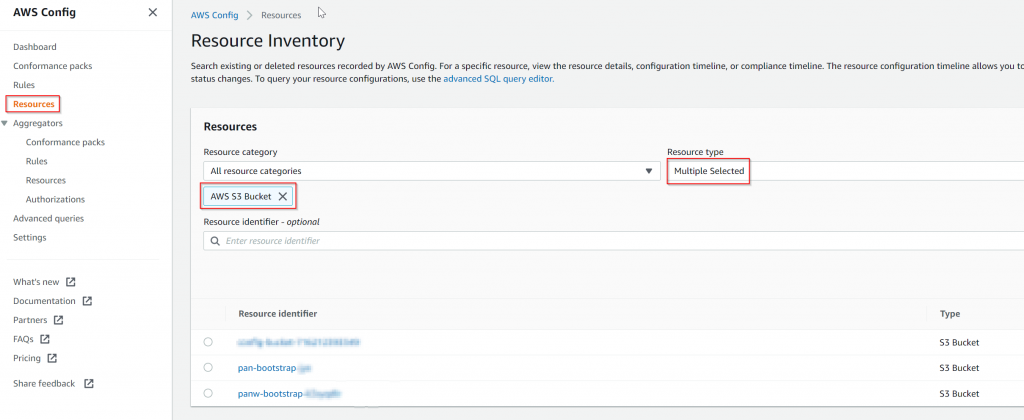
Find the two S3 buckets to compare, notice this is actually under Resources , then filtered by Resource Type = AWS S3 Bucket
In the middle section, expand View Configuration Item (JSON), then copy to your favorite tool for comparison (VS Code / WinMerg)
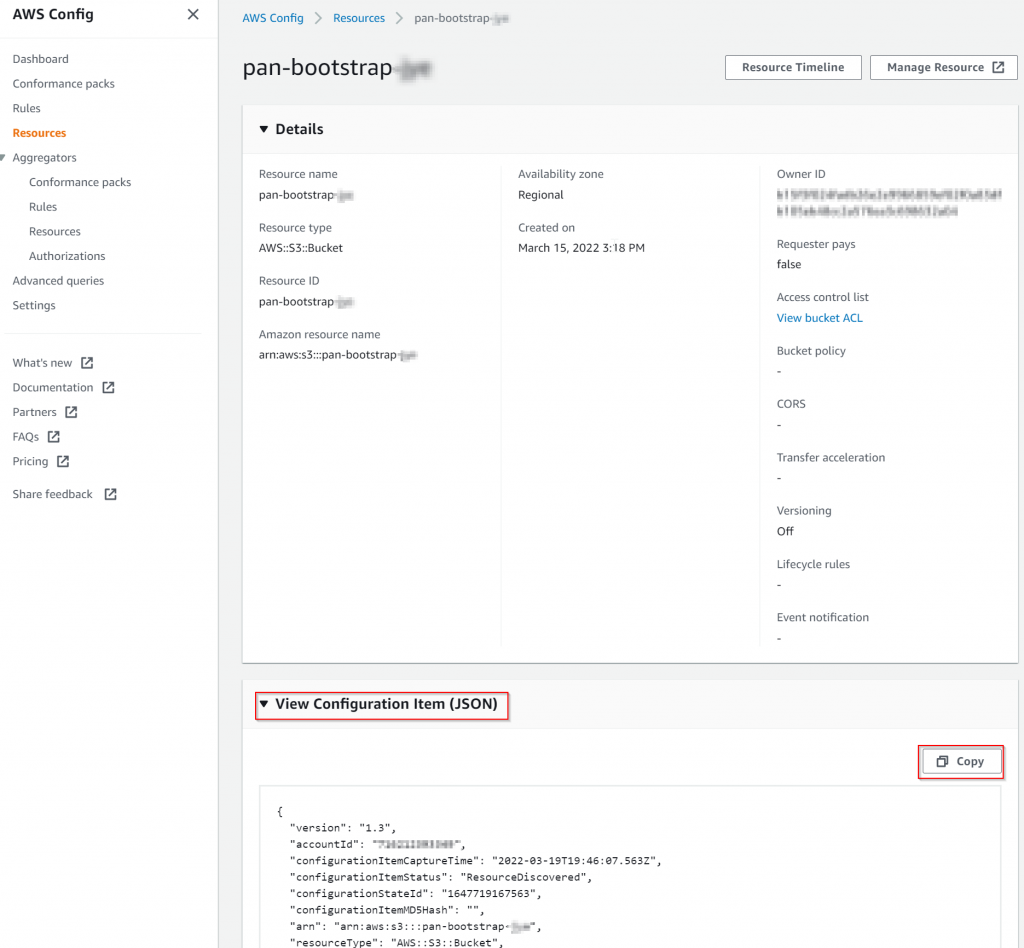
Comparison screenshot:
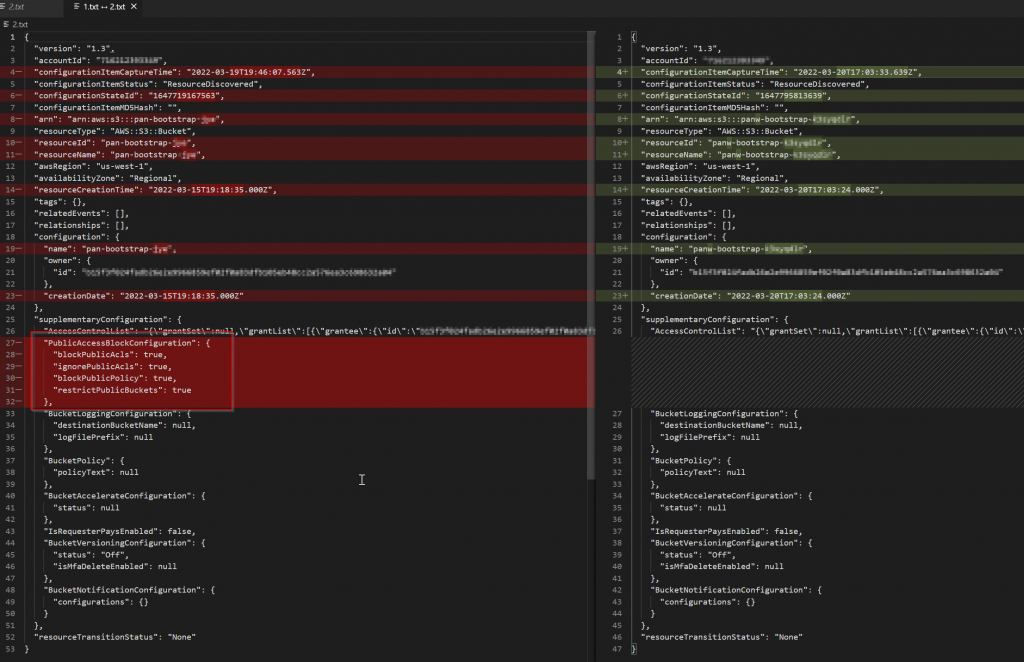
It’s easy to see following section is missing
"PublicAccessBlockConfiguration": {
"blockPublicAcls": true,
"ignorePublicAcls": true,
"blockPublicPolicy": true,
"restrictPublicBuckets": true
},Cleanup
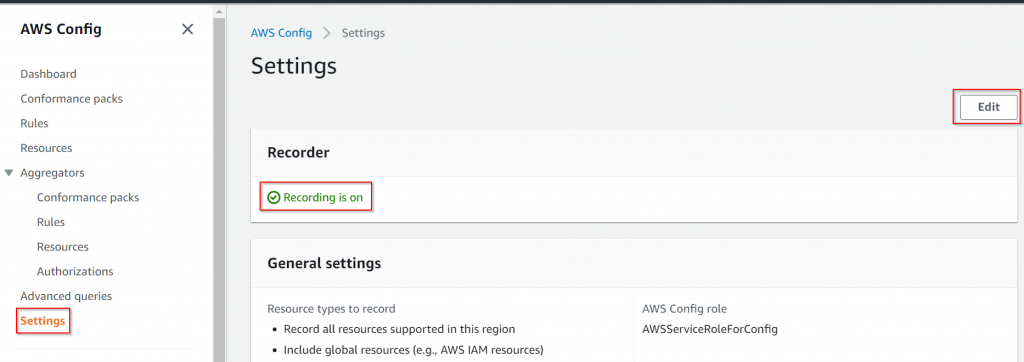
Keep in mind that there is a cost for using AWS Config. If you only need it for comparing resources configuration, after you are done, you should disable it:
Settings -> Note Recording is on -> Edit
Uncheck Enable recording
Confirm
Now that Recording is off

Bootstrap Palo Alto with Aviatrix FireNet with AWS GWLB enabled
Recently I’ve come to figure out how to bootstrap Palo Alto firewall while integrated with AWS GWLB and Aviatrix FireNet, here are my learning journal for future references:
Validated environment:
- Aviatrix Controller version: UserConnect-6.6.5404
- Palo Alto Networks VM-Series Next-Generation Firewall (BYOL) 10.1.3
I’ve used following Terraform code to create an Aviatrix FireNet egress only transit
module "transit_firenet_egress" {
source = "terraform-aviatrix-modules/aws-transit-firenet/aviatrix"
version = "5.0.0"
name = "egress"
cidr = "10.1.0.0/20"
region = var.region
account = var.account
firewall_image = "Palo Alto Networks VM-Series Next-Generation Firewall (BYOL)"
inspection_enabled = false
egress_enabled = true
enable_egress_transit_firenet = true
single_az_ha = false
use_gwlb = true
firewall_image_version = "10.1.3"
}Then followed steps in this article:
- Step 3 can be skipped, as no need to active license
- Step 4 can be skipped, as Firewall is configured as one-armed mode, there’s no WAN port
- Step 6 can be skipped, as again Firewall is one-armed mode, there’s no need for route table changes
After the configuration and confirmed Firewall worked as expected. I’ve saved the configuration as bootstrap.xml
Then I’ve followed this article:
- Created S3 bucket
- Created IAM Role bootstrap-VM-S3-role and Policy bootstrap-VM-S3-policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::*"
]
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::*"
]
}
]
}- Create following folder structure in S3 bucket
bootstrap-bucket/
config/
init-cfg.txt
bootstrap.xml
content/
license/
software/- Uploaded bootstrap.xml and init-cfg.txt
- Modified Terraform code, so it looks like
module "transit_firenet_egress" {
source = "terraform-aviatrix-modules/aws-transit-firenet/aviatrix"
version = "5.0.0"
name = "egress"
cidr = "10.1.0.0/20"
region = var.region
account = var.account
firewall_image = "Palo Alto Networks VM-Series Next-Generation Firewall (BYOL)"
inspection_enabled = false
egress_enabled = true
enable_egress_transit_firenet = true
single_az_ha = false
use_gwlb = true
firewall_image_version = "10.1.3"
bootstrap_bucket_name_1 = "<s3-buck-name>"
iam_role_1 = "bootstrap-VM-S3-role"
}Palo CLI command to check if bootstrap worked:
show system bootstrap statusIn my case, the bootstrap appeared to be working
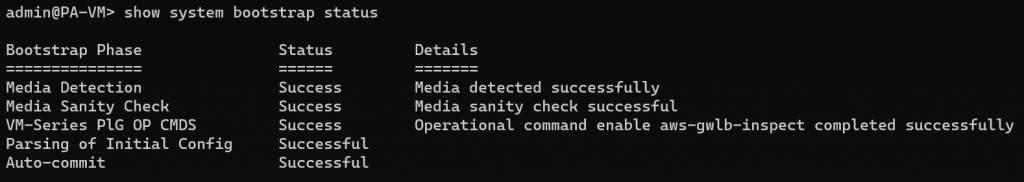
Additional command to troubleshoot bootstrap, or you can watch console session messages
debug logview component bts_detailsHowever when tried to pass traffic through firewall, even when policy is wide open, package capture still shows traffic get dropped when sending from GWLB endpoints
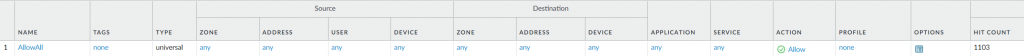
After comparing with a working manually configured firewall with an bootstrapped firewall, here’s the observations:
- When bootstrap.xml loaded via bootstrap, and export the configuration right away, only public-key got modified, which makes sense as new firewall gets new ssh keys
- I’ve also learned that when there’s a conflict setting between init-cfg.txt and bootstrap.xml, the setting in init-cfg.txt wins. Since we are not using Panorama at this point, all values of the init-cfg.txt should be just empty like this:
type=
ip-address=
default-gateway=
netmask=
ipv6-address=
ipv6-default-gateway=
hostname=
vm-auth-key=
panorama-server=
panorama-server-2=
tplname=
dgname=
dns-primary=
dns-secondary=
op-command-modes=
dhcp-send-hostname=
dhcp-send-client-id=
dhcp-accept-server-hostname=
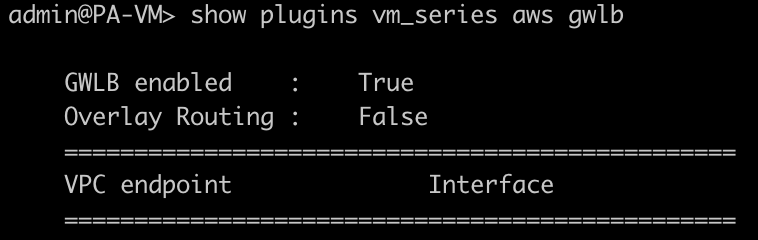
dhcp-accept-server-domain=- We also found out when using bootstrap with terraform, the GWLB isn’t enabled, CLI command to check:
show plugins vm_series aws gwlb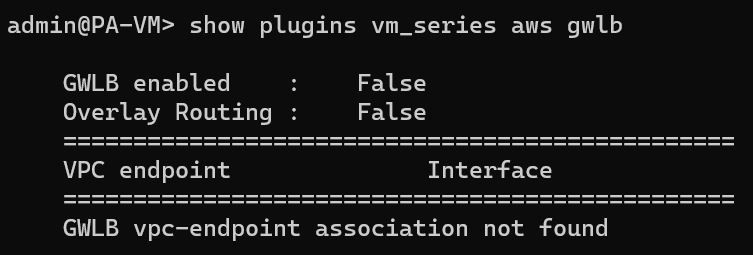
- The management interface however has been swapped as expected
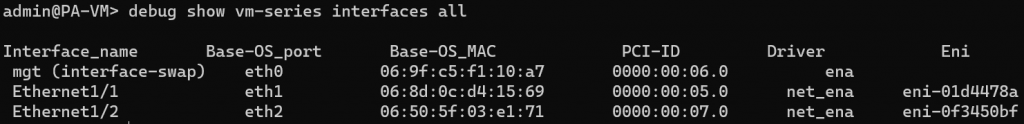
- Since we do need to use GWLB to pass traffic to the firewall, tried following command:
request plugins vm_series aws gwlb inspect enable yesNow the GWLB is enabled, and traffic is passing!
We modified init-cfg.txt to also enable GWLB during bootstrapping
type=
ip-address=
default-gateway=
netmask=
ipv6-address=
ipv6-default-gateway=
hostname=
vm-auth-key=
panorama-server=
panorama-server-2=
tplname=
dgname=
dns-primary=
dns-secondary=
op-command-modes=
dhcp-send-hostname=
dhcp-send-client-id=
dhcp-accept-server-hostname=
dhcp-accept-server-domain=
plugin-op-commands=aws-gwlb-inspect:enableNow everything is working as expected, reference:
Terraform code to create S3 bucket, role/ policy and sample bootstrap.xml and init-cfg.txt:
https://github.com/jye-aviatrix/terraform-aviatrix-aws-gwlb-palo-alto-10-bootstrap
