This is the first of the three articles. It will be the easiest to accomplish but with following requirements, and constrains highlighted.
- Virtual Private Gateway (VGW) has to be created in the same region as the Direct Connect Private Virtual Interface (VIF).
- Each VIF is dedicated to one VGW.
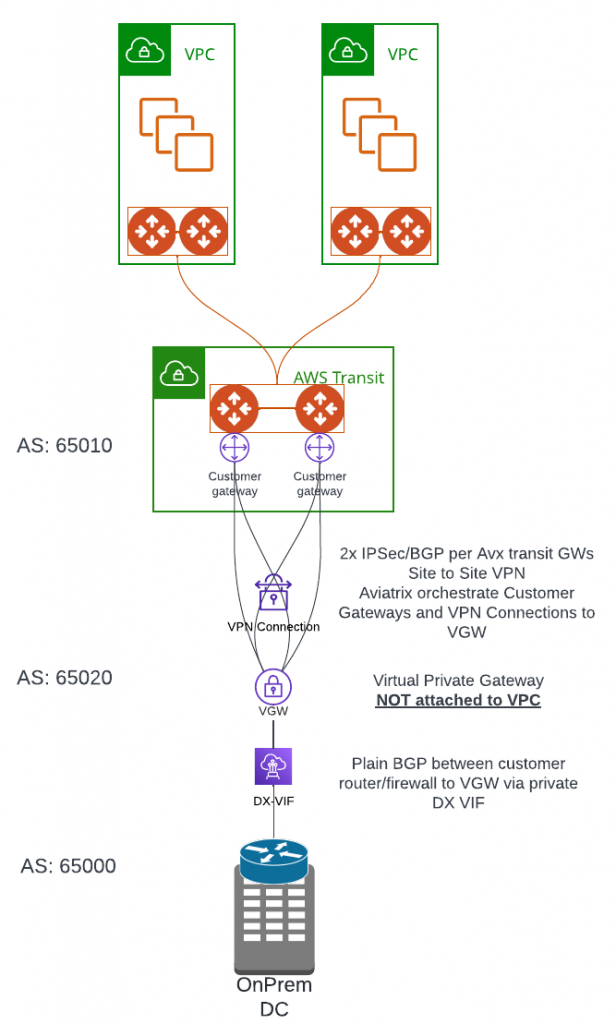
- VGW is NOT attached to the VPC
- Aviatrix orchestrate Customer Gateways and VPN Connections, building 2x IPSec/BGP tunnels per Aviatrix Transit Gateway.
- Each IPSec tunnel have 1.25G throughput limit
- Private Virtual Interface support up to 100 BGP routes, BGP session will go DOWN when more routes been advertised. In layman’s term when this happens, Cloud won’t see OnPrem routes, and OnPrem won’t see Cloud routes, connectivity between Cloud and OnPrem will be LOST. You must summarize advertised routes on both ends to be lower than 100 to get around this limit.
- Between On-Premise to VGW, traffic maybe protected by MACSec, but still expose to man in the middle attack. Reference article: Securing your network connection to the cloud: MACSec vs. IPSec
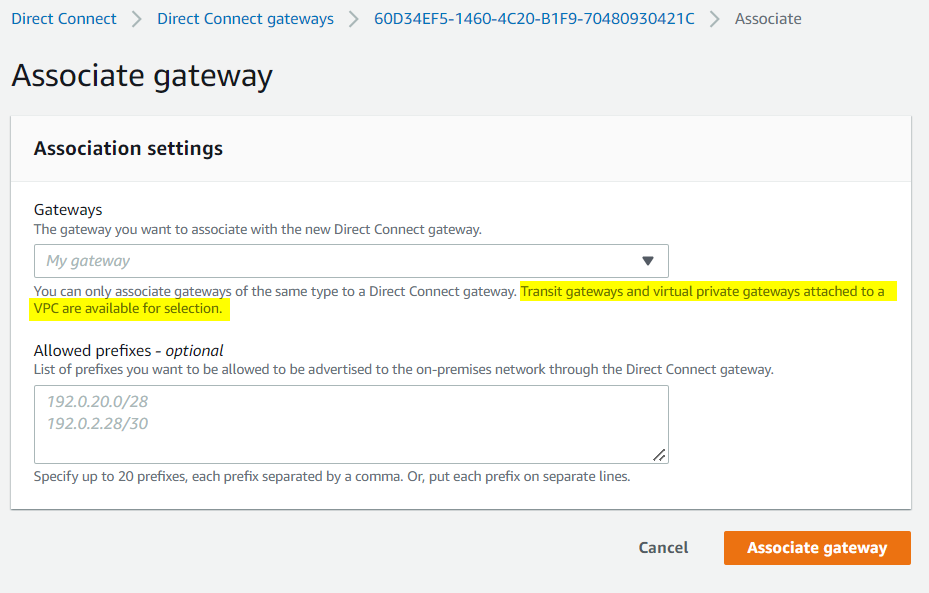
A side note: Direct Connect Gateway can NOT be used here. As VGW is NOT attached to a VPC
Steps to create the connection
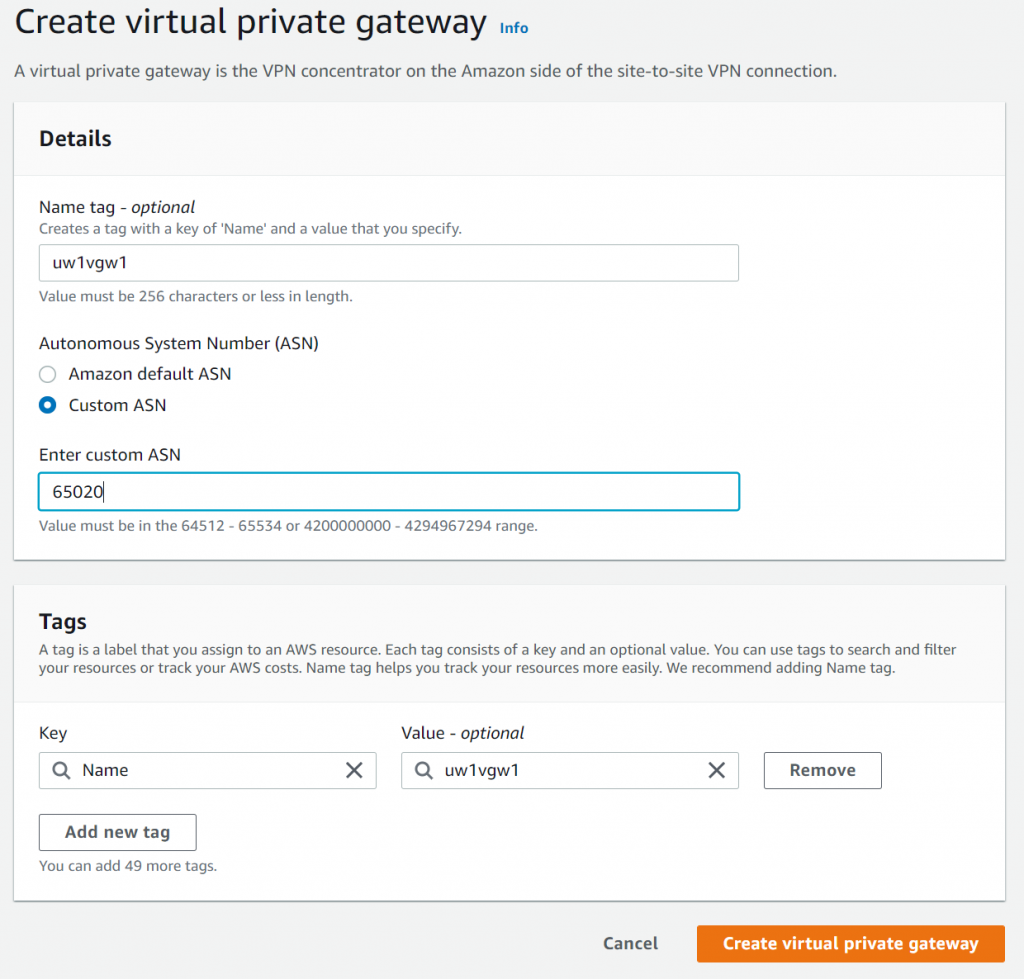
- In the same region of Aviatrix Transit Gateway, create Virtual Private Gateway and specify and custom ASN number
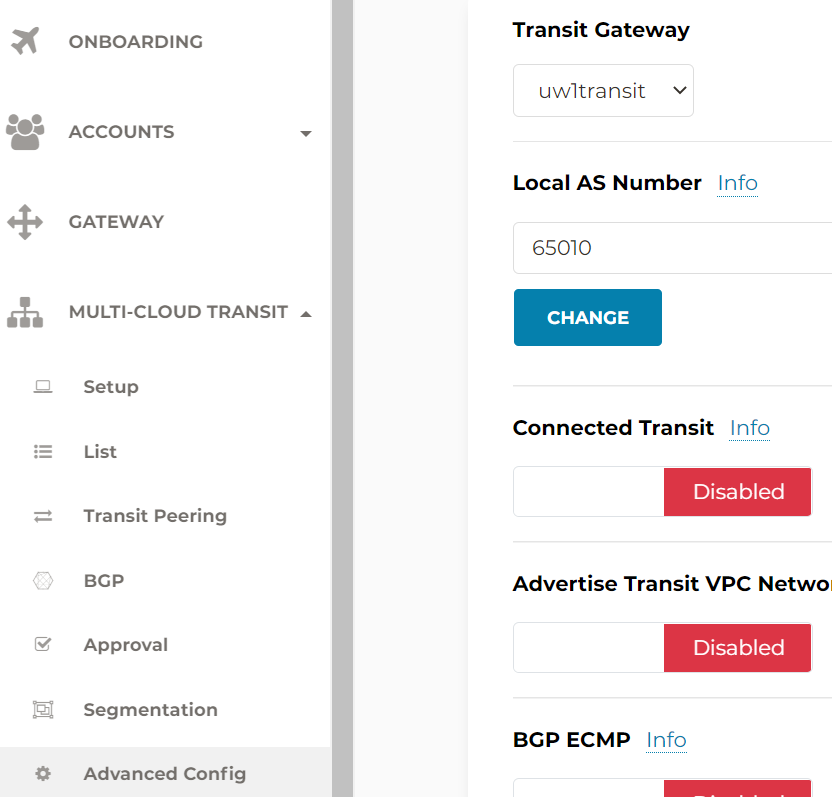
- In Aviatrix Transit gateway, make sure to specify ASN number
- In Aviatrix Multi-Cloud Transit menu, add newly created VGW as external connection, note if you have attached VGW to VPC, and error would occur.
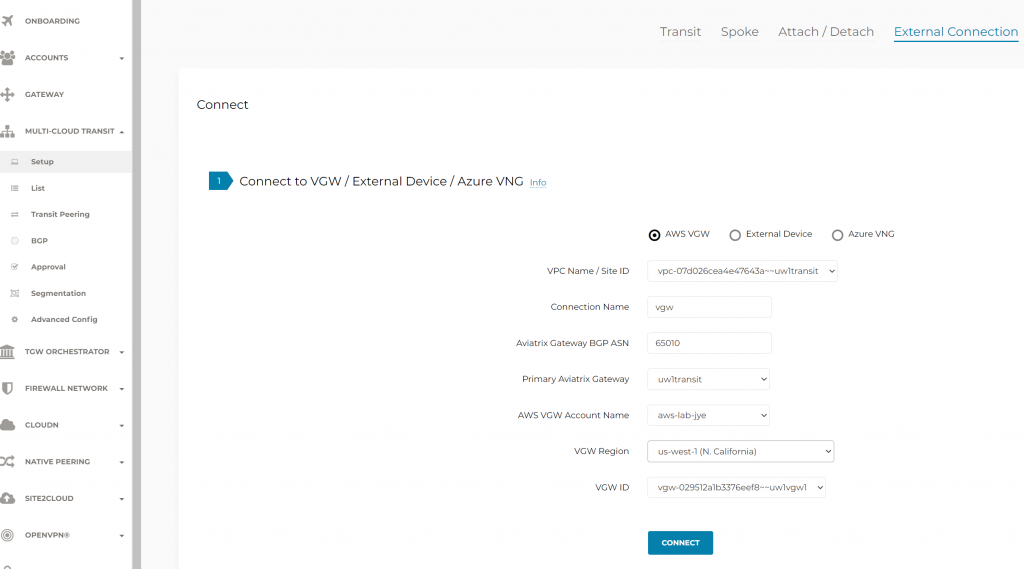
- After the external connection workflow is completed, you will observe in AWS console that customer gateways and Site-to-Site VPN connections got created automatically
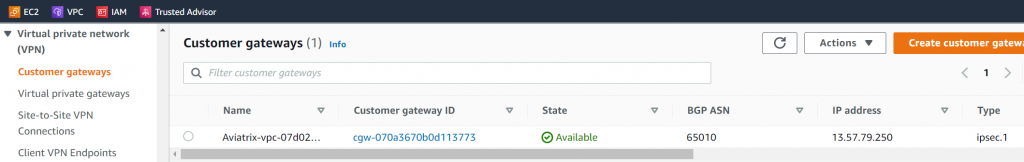
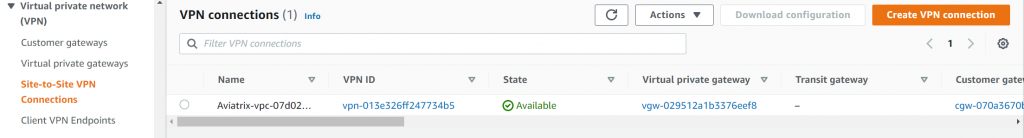
- Observe in Aviatrix Site2Cloud menu, a connection have been created
- In CoPilot, eventually (it take a few minutes for the VPN connection and BGP session to be up. AWS VGW does not proactively initiate connections, be patient!)
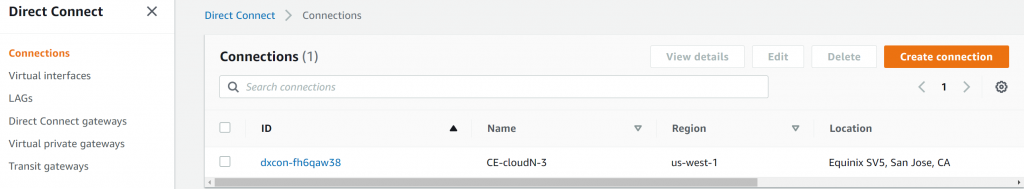
- Get a DX connection to your account, and note down VLAN number, accept the connection and wait a few min for it to be established.
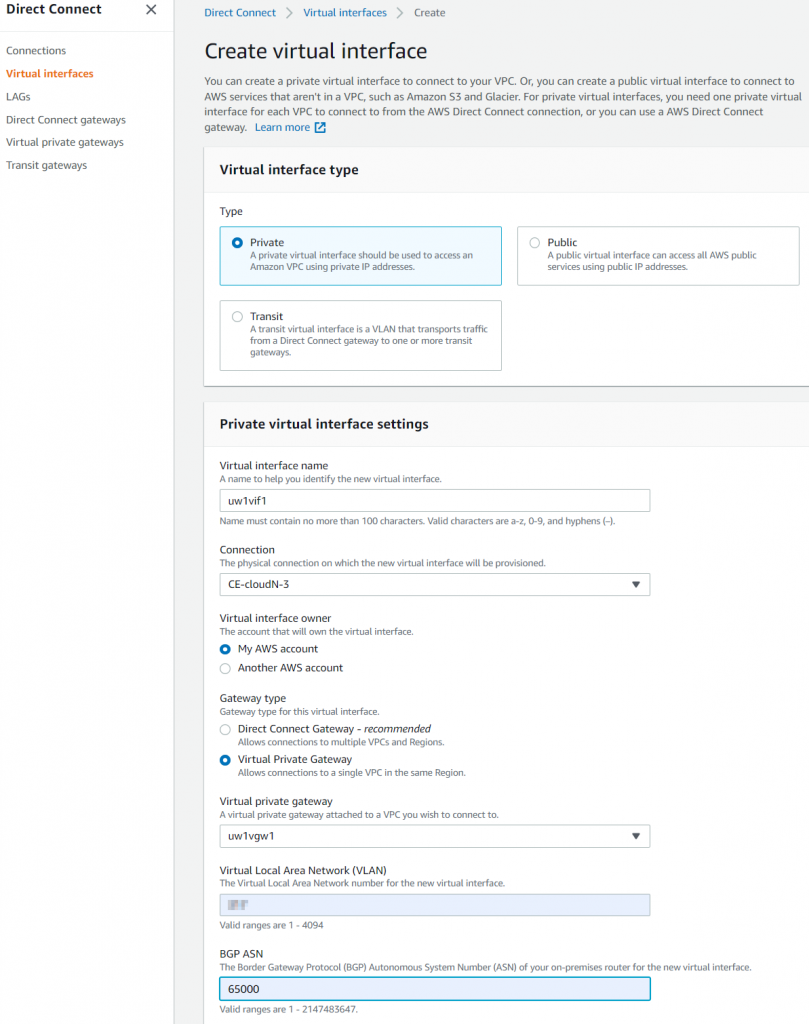
- Create Virtual Interface
- Pick the connection created earlier
- Pick Virtual Private Gateway as the Gateway type and pick the VGW created earlier
- Enter the VLAN number of the connection (Will error out if wrong VLAN number entered)
- Enter your OnPrem device BGP ASN
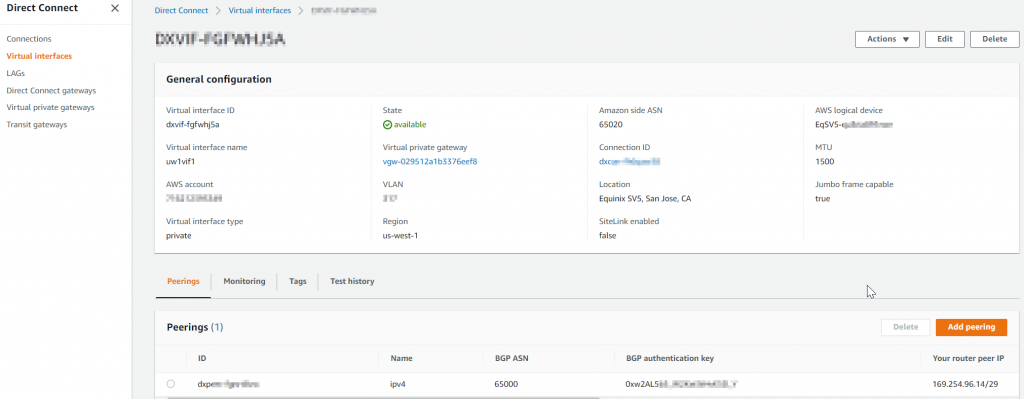
- Open the VIF just created and note down
- Your router peer IP <- IP that you need to set on your router/firewall
- Amazon router peer IP < IP of the VIF, try to ping from your router to it to make sure L2 connectivity is there
- BGP authentication key
- Last configure your router/firewall to establish BGP connection with VIF.
Configure interface on your router to use the 169.254.x.x address listed in VIF configuration. Note the VLAN number isn’t the same as the DX Connection VLAN number, this depends on your physical connectivity to your upstream switch.
interface GigabitEthernet0/0/0.512
description connected to VIF
encapsulation dot1Q 512
ip address 169.254.96.14 255.255.255.248Ping the 169.254.x.x IP on the AWS side to make sure there’s L2 connectivity
#ping 169.254.96.9 source 169.254.96.14
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 169.254.96.9, timeout is 2 seconds:
Packet sent with a source address of 169.254.96.14
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 msBGP Configuration, remote AS point to VGW’s ASN number
router bgp 65000
bgp log-neighbor-changes
neighbor 169.254.96.9 remote-as 65020
neighbor 169.254.96.9 password <BGP authentication key from VIF>
!
address-family ipv4
neighbor 169.254.96.9 activate
neighbor 169.254.96.9 soft-reconfiguration inboundCheck to make sure BGP is up
#show ip bgp summary
BGP router identifier 192.168.77.1, local AS number 65000
BGP table version is 29, main routing table version 29
4 network entries using 992 bytes of memory
4 path entries using 544 bytes of memory
1/1 BGP path/bestpath attribute entries using 280 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 1816 total bytes of memory
BGP activity 16/12 prefixes, 16/12 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
169.254.96.9 4 65030 16460 17602 29 0 0 5d14h 0
At this point Aviatrix Transit should start to receive BGP routes from On-Premise, and On-Premise should receive cloud routes from Aviatrix Transit.
To validate from OnPrem
show ip bgp
show ip bgp neighbors 169.254.96.9 received-routes
show ip bgp neighbors 169.254.96.9 advertised-routesTo validate from Aviatrix
Aviatrix Controller -> Multi-Cloud Transit -> BGP -> Diagnostics -> Select Transit connected to DX -> Run one of the BGP command above
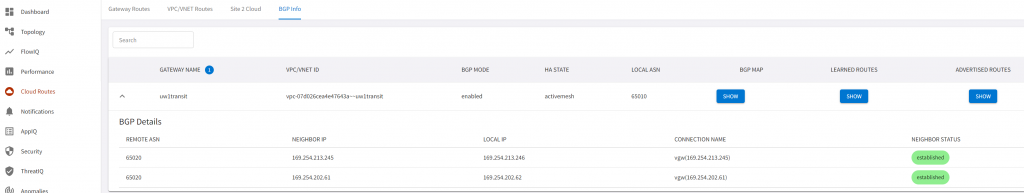
Aviatrix CoPilot -> Cloud Routes -> BGP Info -> Select Transit connected to DX -> Learned Routes/Advertised Routes
