So you have created your resources manually in AWS and it works fine, but when you tried to create the resource using Terraform and it just won’t work?
I’ve ran into this issue when tried to create S3 + Policy + Roles for Palo Alto bootstrap, and here below is how to resolve this, please feel free to comment if you have better methods.
Background:
I’ve followed this article and created S3 bucket, folder structure, uploaded bootstrap.xml and init-cfg.txt under config folder and it works fine. But when I tried to terraform scripts from my buddy and it just doesn’t work. There must be some delta that’s causing the issue.
It’s a very easy problem to tackle in Azure, for most resources, you can choose to export to ARM or BICEP template, which will reveal all configurations.
It isn’t as straight forward in AWS, when I’m looking at AWS CLI, aws s3 command have following subcommands
$ aws s3 ?
usage: aws [options] <command> <subcommand> [<subcommand> ..] [parameters]
To see help text, you can run:
aws help
aws <command> help
aws <command> <subcommand> help
aws: error: argument subcommand: Invalid choice, valid choices are:
ls | website
cp | mv
rm | sync
mb | rb
presignNone of them related to describe the current configuration
There is an s3api command, but it appears that you must query each subcommands, such as following huge list, what if my solution is much more complicated than just S3, then this will snowball much quicker to manage
get-bucket-accelerate-configuration
get-bucket-acl
get-bucket-analytics-configuration
get-bucket-cors
get-bucket-encryption
get-bucket-intelligent-tiering-configuration
get-bucket-inventory-configuration
get-bucket-lifecycle-configuration
get-bucket-location
get-bucket-logging
get-bucket-metrics-configuration
get-bucket-notification-configuration
get-bucket-ownership-controls
get-bucket-policy
get-bucket-policy-status
get-bucket-replication
get-bucket-request-payment
get-bucket-tagging
get-bucket-versioning
get-bucket-website
get-object
get-object-acl
get-object-attributes
get-object-legal-hold
get-object-lock-configuration
get-object-retention
get-object-tagging
get-object-torrent
get-public-access-blockThen I’ve come across AWS Config, which should track configuration of each resources
AWS Config – Getting started
- First goes to the region of the resources you want to track, and search for Config

- Click on Get started. I have selected Include global resources as there’s a need to track roles and policies and choose to create a new bucket
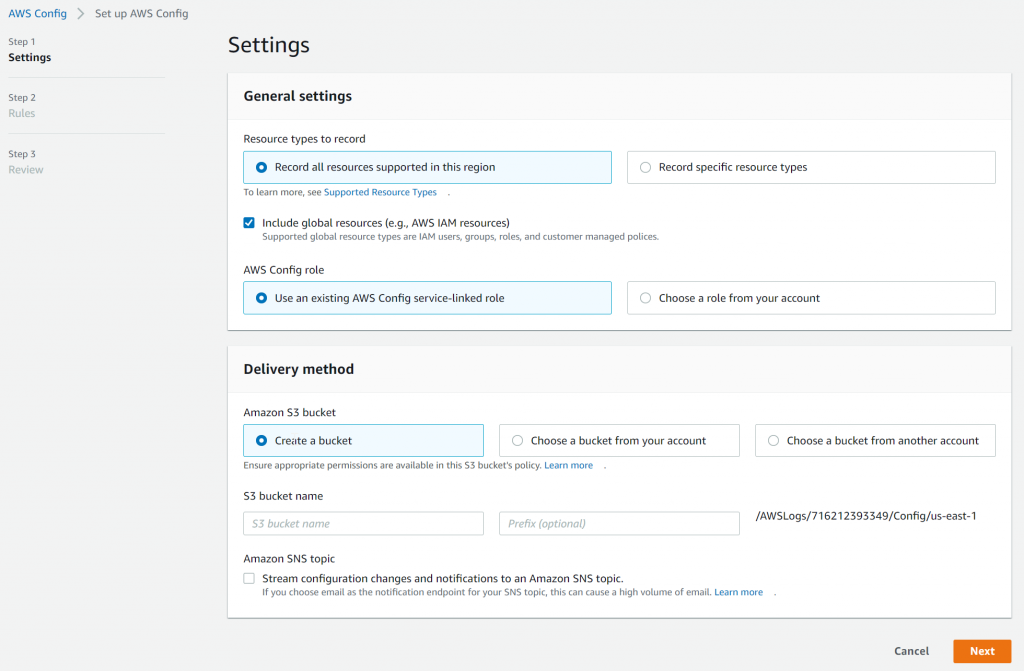
- Rules are meant to be auditing purpose to evaluate if your resources is following best practices, which isn’t useful for my situation, so I didn’t select anything

- Finally review and confirm

AWS Config – comparing resources
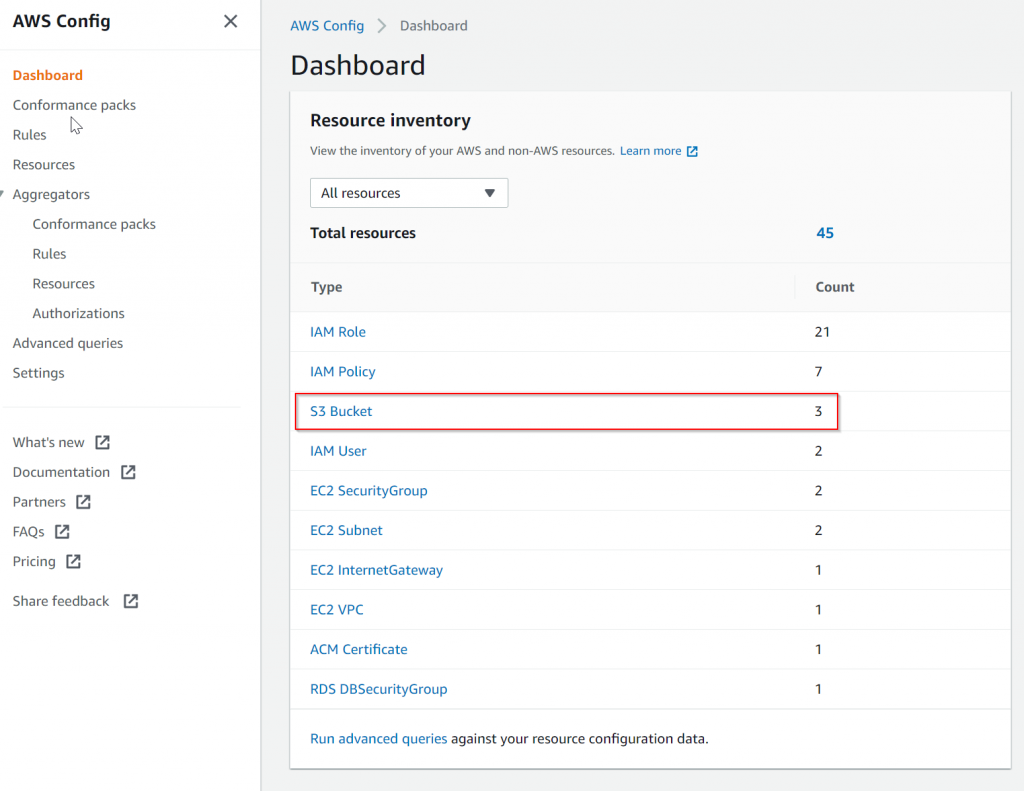
Going to AWS Config -> Dashboard, it nicely listed all discovered resources by category. Since we need to compare the S3 configuration, then I’ve clicked on S3 Bucket
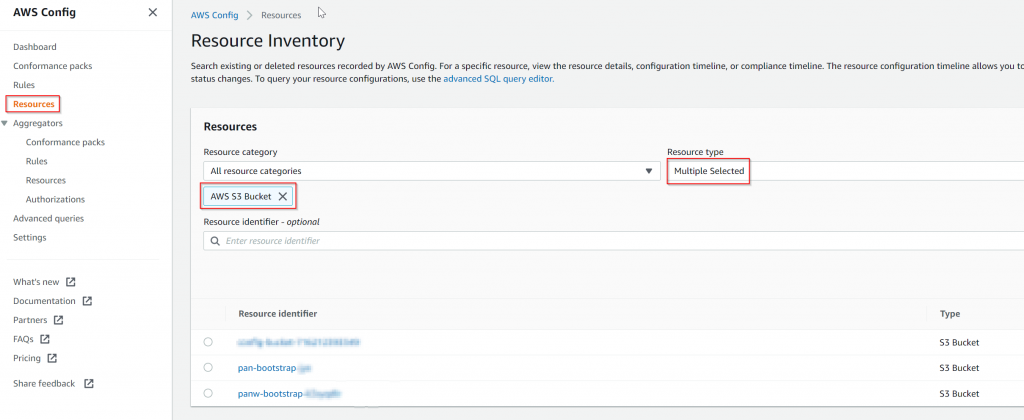
Find the two S3 buckets to compare, notice this is actually under Resources , then filtered by Resource Type = AWS S3 Bucket
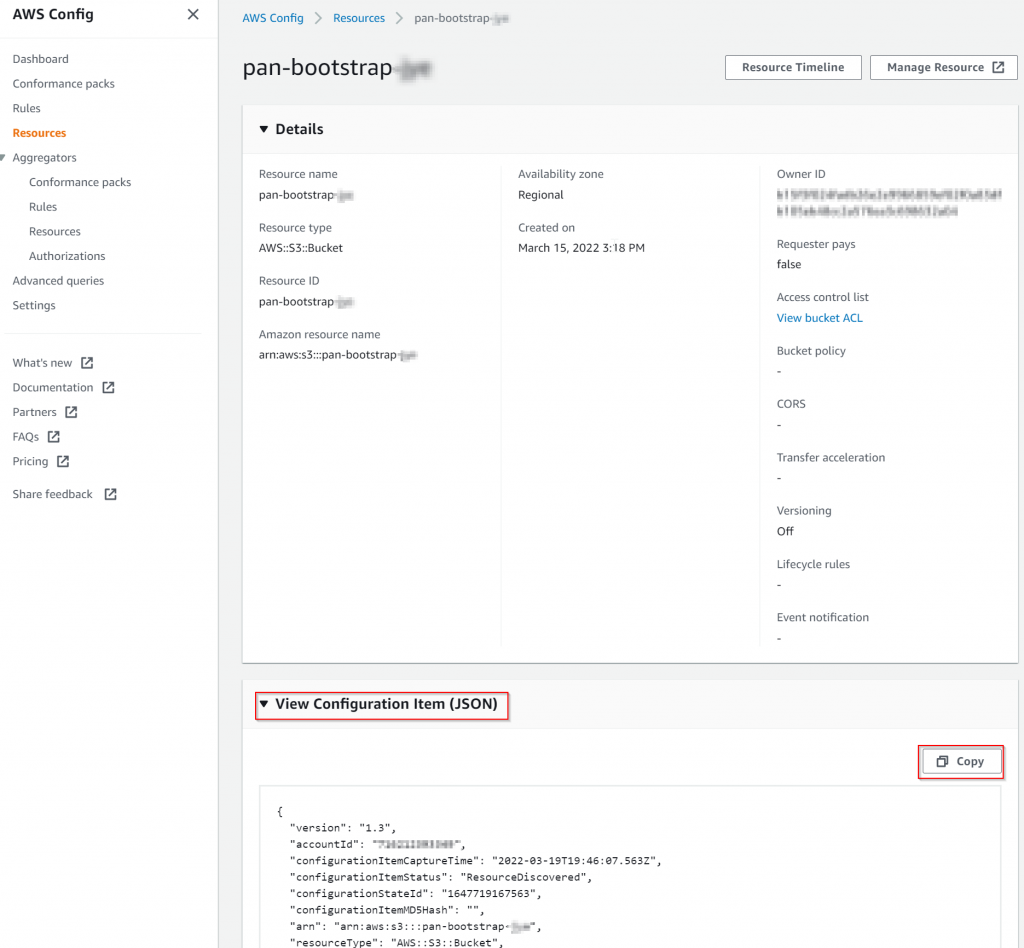
In the middle section, expand View Configuration Item (JSON), then copy to your favorite tool for comparison (VS Code / WinMerg)
Comparison screenshot:
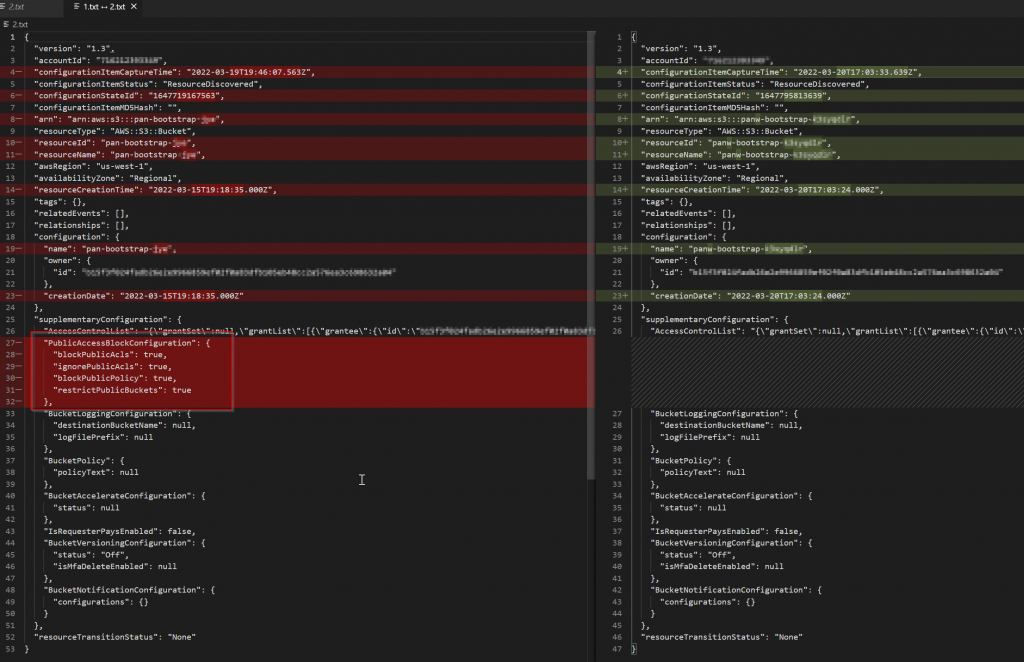
It’s easy to see following section is missing
"PublicAccessBlockConfiguration": {
"blockPublicAcls": true,
"ignorePublicAcls": true,
"blockPublicPolicy": true,
"restrictPublicBuckets": true
},Cleanup
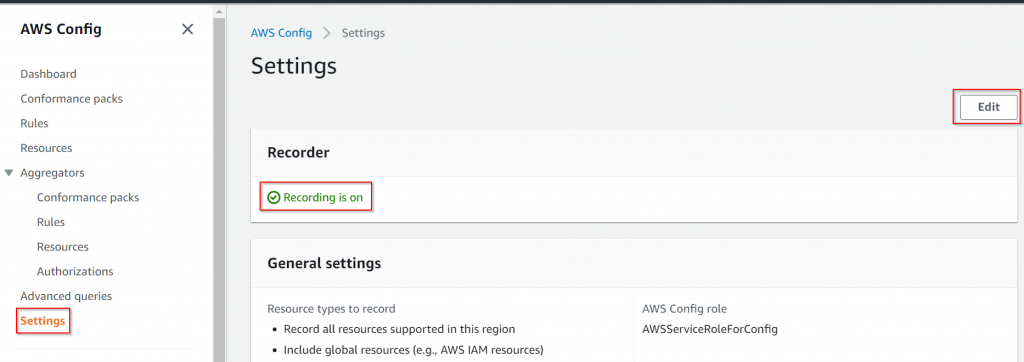
Keep in mind that there is a cost for using AWS Config. If you only need it for comparing resources configuration, after you are done, you should disable it:
Settings -> Note Recording is on -> Edit
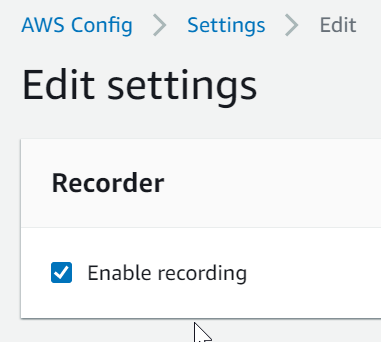
Uncheck Enable recording
Confirm
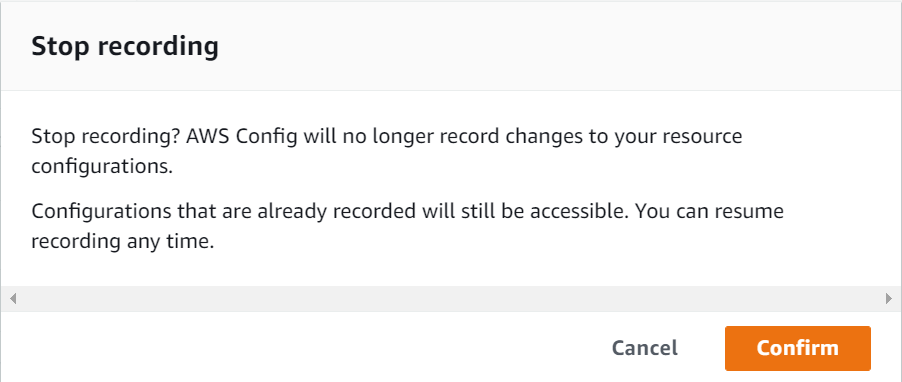
Now that Recording is off

