So I’ve got this block of terraform code, which simply just allow the role to assume role
data "aws_iam_policy_document" "bootstrap_role" {
statement {
actions = ["sts:AssumeRole"]
principals {
type = "Service"
identifiers = ["ec2.amazonaws.com"]
}
}
}
resource "aws_iam_role" "bootstrap" {
name = "bootstrap-${random_string.bucket.result}"
assume_role_policy = data.aws_iam_policy_document.bootstrap_role.json
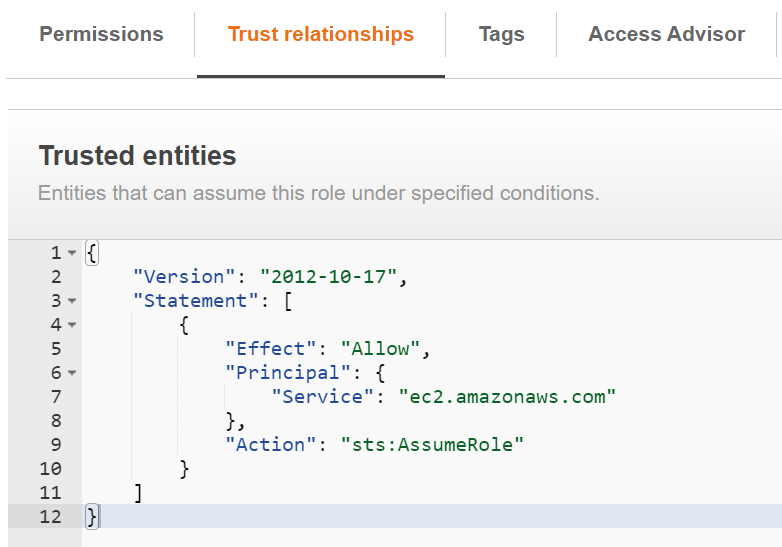
}When check in AWS Console, I can see following Trust relationships created with:
“Sid”: “”
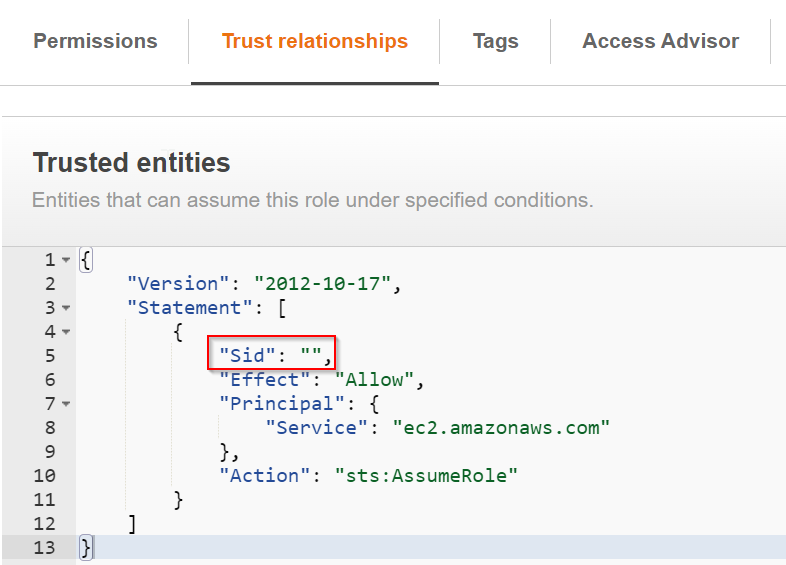
When I would create the role in AWS Console, I would not have this section:
“Sid”: “”
Tried to update the terraform code to following, and it made no difference:
data "aws_iam_policy_document" "bootstrap_role" {
statement {
actions = ["sts:AssumeRole"]
principals {
type = "Service"
identifiers = ["ec2.amazonaws.com"]
}
sid = null
}
}
resource "aws_iam_role" "bootstrap" {
name = "bootstrap-${random_string.bucket.result}"
assume_role_policy = data.aws_iam_policy_document.bootstrap_role.json
}After some research, I’ve settled with this code with incline JSON policy instead
resource "aws_iam_role" "bootstrap" {
name = "bootstrap-${random_string.bucket.result}"
assume_role_policy = jsonencode(
{
"Version" : "2012-10-17",
"Statement" : [
{
"Effect" : "Allow",
"Principal" : {
"Service" : "ec2.amazonaws.com"
},
"Action" : "sts:AssumeRole"
}
]
}
)
}Now it’s nice and clean