Recently I’ve come to figure out how to bootstrap Palo Alto firewall while integrated with AWS GWLB and Aviatrix FireNet, here are my learning journal for future references:
Validated environment:
- Aviatrix Controller version: UserConnect-6.6.5404
- Palo Alto Networks VM-Series Next-Generation Firewall (BYOL) 10.1.3
I’ve used following Terraform code to create an Aviatrix FireNet egress only transit
module "transit_firenet_egress" {
source = "terraform-aviatrix-modules/aws-transit-firenet/aviatrix"
version = "5.0.0"
name = "egress"
cidr = "10.1.0.0/20"
region = var.region
account = var.account
firewall_image = "Palo Alto Networks VM-Series Next-Generation Firewall (BYOL)"
inspection_enabled = false
egress_enabled = true
enable_egress_transit_firenet = true
single_az_ha = false
use_gwlb = true
firewall_image_version = "10.1.3"
}Then followed steps in this article:
- Step 3 can be skipped, as no need to active license
- Step 4 can be skipped, as Firewall is configured as one-armed mode, there’s no WAN port
- Step 6 can be skipped, as again Firewall is one-armed mode, there’s no need for route table changes
After the configuration and confirmed Firewall worked as expected. I’ve saved the configuration as bootstrap.xml
Then I’ve followed this article:
- Created S3 bucket
- Created IAM Role bootstrap-VM-S3-role and Policy bootstrap-VM-S3-policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::*"
]
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::*"
]
}
]
}- Create following folder structure in S3 bucket
bootstrap-bucket/
config/
init-cfg.txt
bootstrap.xml
content/
license/
software/- Uploaded bootstrap.xml and init-cfg.txt
- Modified Terraform code, so it looks like
module "transit_firenet_egress" {
source = "terraform-aviatrix-modules/aws-transit-firenet/aviatrix"
version = "5.0.0"
name = "egress"
cidr = "10.1.0.0/20"
region = var.region
account = var.account
firewall_image = "Palo Alto Networks VM-Series Next-Generation Firewall (BYOL)"
inspection_enabled = false
egress_enabled = true
enable_egress_transit_firenet = true
single_az_ha = false
use_gwlb = true
firewall_image_version = "10.1.3"
bootstrap_bucket_name_1 = "<s3-buck-name>"
iam_role_1 = "bootstrap-VM-S3-role"
}Palo CLI command to check if bootstrap worked:
show system bootstrap statusIn my case, the bootstrap appeared to be working
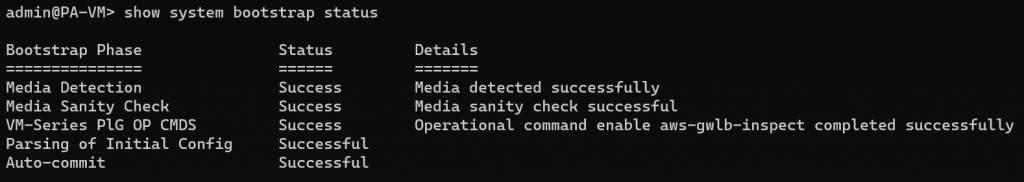
Additional command to troubleshoot bootstrap, or you can watch console session messages
debug logview component bts_detailsHowever when tried to pass traffic through firewall, even when policy is wide open, package capture still shows traffic get dropped when sending from GWLB endpoints
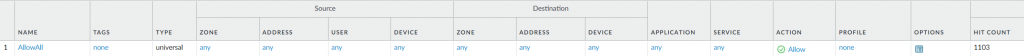
After comparing with a working manually configured firewall with an bootstrapped firewall, here’s the observations:
- When bootstrap.xml loaded via bootstrap, and export the configuration right away, only public-key got modified, which makes sense as new firewall gets new ssh keys
- I’ve also learned that when there’s a conflict setting between init-cfg.txt and bootstrap.xml, the setting in init-cfg.txt wins. Since we are not using Panorama at this point, all values of the init-cfg.txt should be just empty like this:
type=
ip-address=
default-gateway=
netmask=
ipv6-address=
ipv6-default-gateway=
hostname=
vm-auth-key=
panorama-server=
panorama-server-2=
tplname=
dgname=
dns-primary=
dns-secondary=
op-command-modes=
dhcp-send-hostname=
dhcp-send-client-id=
dhcp-accept-server-hostname=
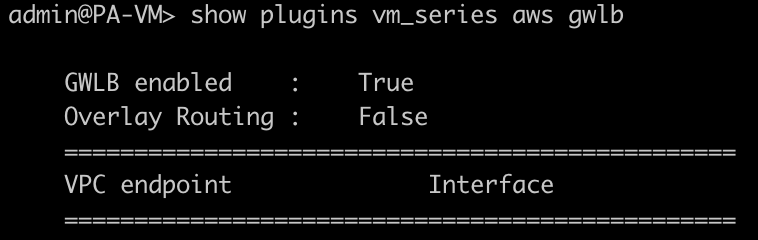
dhcp-accept-server-domain=- We also found out when using bootstrap with terraform, the GWLB isn’t enabled, CLI command to check:
show plugins vm_series aws gwlb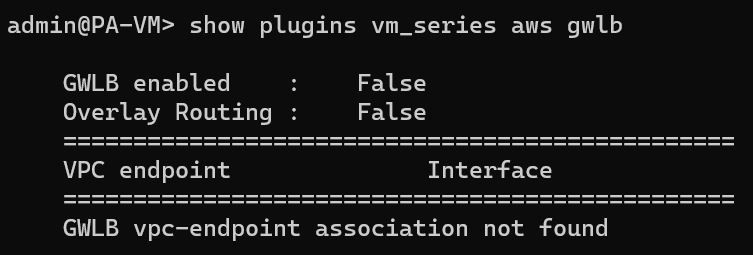
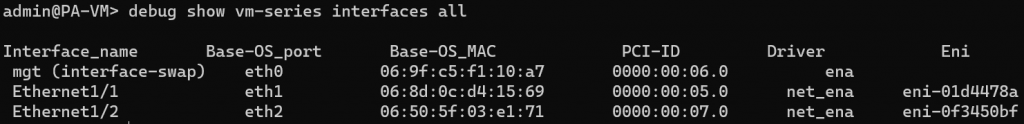
- The management interface however has been swapped as expected
- Since we do need to use GWLB to pass traffic to the firewall, tried following command:
request plugins vm_series aws gwlb inspect enable yesNow the GWLB is enabled, and traffic is passing!
We modified init-cfg.txt to also enable GWLB during bootstrapping
type=
ip-address=
default-gateway=
netmask=
ipv6-address=
ipv6-default-gateway=
hostname=
vm-auth-key=
panorama-server=
panorama-server-2=
tplname=
dgname=
dns-primary=
dns-secondary=
op-command-modes=
dhcp-send-hostname=
dhcp-send-client-id=
dhcp-accept-server-hostname=
dhcp-accept-server-domain=
plugin-op-commands=aws-gwlb-inspect:enableNow everything is working as expected, reference:
Terraform code to create S3 bucket, role/ policy and sample bootstrap.xml and init-cfg.txt:
https://github.com/jye-aviatrix/terraform-aviatrix-aws-gwlb-palo-alto-10-bootstrap
