Resource aviatrix_vpc creates a VPC/vNet/VCN in various cloud types. For Aviatrix Transit VPC, there would be various different subnets created for the purpose of integrating with SDWan appliances, insertion of Firewalls, integration with AWS TGW (Aviatrix Orchestrated), or utilizing AWS Gateway Load Balancer etc.
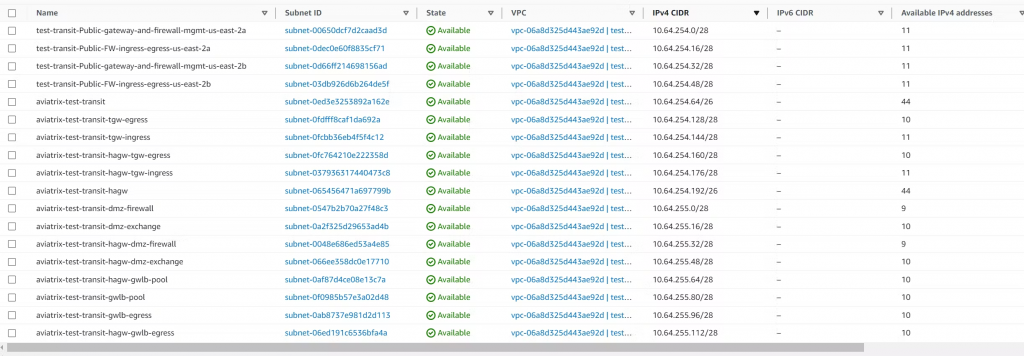
An example of subnets created in AWS for Aviatrix Transit VPC with High-Performance Encryption, TGW-O integration, and Firewall integration with GWLB.
aviatrix_vpc resource object with name region1_ew_firenet, would have following content
> aviatrix_vpc.region1_ew_firenet
{
"account_name" = "aws-lab"
"availability_domains" = tolist([])
"aviatrix_firenet_vpc" = true
"aviatrix_transit_vpc" = false
"azure_vnet_resource_id" = tostring(null)
"cidr" = "10.100.128.0/23"
"cloud_type" = 1
"enable_native_gwlb" = false
"enable_private_oob_subnet" = false
"fault_domains" = tolist([])
"id" = "ue1-ew-firenet"
"name" = "ue1-ew-firenet"
"num_of_subnet_pairs" = tonumber(null)
"private_mode_subnets" = false
"private_subnets" = tolist([])
"public_subnets" = tolist([
{
"cidr" = "10.100.128.0/28"
"name" = "ue1-ew-firenet-Public-gateway-and-firewall-mgmt-us-east-1a"
"subnet_id" = "subnet-0207386fd45f13cf2"
},
{
"cidr" = "10.100.128.16/28"
"name" = "ue1-ew-firenet-Public-FW-ingress-egress-us-east-1a"
"subnet_id" = "subnet-0403cbe5100a5945c"
},
{
"cidr" = "10.100.128.32/28"
"name" = "ue1-ew-firenet-Public-gateway-and-firewall-mgmt-us-east-1b"
"subnet_id" = "subnet-0a43b6f28b5eb88a6"
},
{
"cidr" = "10.100.128.48/28"
"name" = "ue1-ew-firenet-Public-FW-ingress-egress-us-east-1b"
"subnet_id" = "subnet-09341d45fdfbf24bc"
},
])
"region" = "us-east-1"
"resource_group" = tostring(null)
"route_tables" = tolist([
"rtb-0bc87db01bd3574d8",
"rtb-0e4ad8aa554f1b83f",
"rtb-0c43ff50047c5c660",
"rtb-0cfe274b484b5a8a3",
"rtb-004e80e2c046768d3",
"rtb-077653aaf6f9bc65b",
"rtb-0add1518acb0bab5b",
])
"subnet_size" = tonumber(null)
"subnets" = tolist([
{
"cidr" = "10.100.128.0/28"
"name" = "ue1-ew-firenet-Public-gateway-and-firewall-mgmt-us-east-1a"
"region" = ""
"subnet_id" = "subnet-0207386fd45f13cf2"
},
{
"cidr" = "10.100.128.16/28"
"name" = "ue1-ew-firenet-Public-FW-ingress-egress-us-east-1a"
"region" = ""
"subnet_id" = "subnet-0403cbe5100a5945c"
},
{
"cidr" = "10.100.128.32/28"
"name" = "ue1-ew-firenet-Public-gateway-and-firewall-mgmt-us-east-1b"
"region" = ""
"subnet_id" = "subnet-0a43b6f28b5eb88a6"
},
{
"cidr" = "10.100.128.48/28"
"name" = "ue1-ew-firenet-Public-FW-ingress-egress-us-east-1b"
"region" = ""
"subnet_id" = "subnet-09341d45fdfbf24bc"
},
])
"vpc_id" = "vpc-094f072505996b378"
}Occasionally in your Terraform programming, you will need to reference these subnets by their CIDR range, here below is an example of deploying a Palo Firewall associated with the primary Aviatrix Transit Gateway.
Eg:
egress_subnet needs to reference a public subnet name containing: Public-FW-ingress-egress
management_subnet needs to reference a public subnet name containing: Public-gateway-and-firewall-mgmt
In Terraform version 1.5 and later, a function strcontains has been introduced to provide a boolean value if a string contains a substring.
In the following example:
egress_subnet = element([for s in aviatrix_vpc.region1_ew_firenet.public_subnets : s[“cidr”] if strcontains(s[“name”], “Public-FW-ingress-egress”)], 0)
In public_subnets list, get the list of cidrs for the subnets name containing “Public-FW-ingress-egress” sub-string.
Then use element function to retrieve the first cidr in the list using index of 0
resource "aviatrix_firewall_instance" "region1_ew_fw_1" {
firewall_name = "${var.region1_code}-ew-fw-1"
firewall_size = "m5.xlarge"
vpc_id = aviatrix_vpc.region1_ew_firenet.vpc_id
firewall_image = "Palo Alto Networks VM-Series Next-Generation Firewall (BYOL)"
firewall_image_version = "11.0.2"
egress_subnet = element([for s in aviatrix_vpc.region1_ew_firenet.public_subnets : s["cidr"] if strcontains(s["name"], "Public-FW-ingress-egress")], 0)
firenet_gw_name = aviatrix_transit_gateway.region1_ew_transit_firenet.gw_name
management_subnet = element([for s in aviatrix_vpc.region1_ew_firenet.public_subnets : s["cidr"] if strcontains(s["name"], "Public-gateway-and-firewall-mgmt")], 0)
}If we are going to deploy another Firewall instance, we just have to use the element function to retrieve the second cidr in the list using index of 1
egress_subnet = element([for s in aviatrix_vpc.region1_ew_firenet.public_subnets : s[“cidr”] if strcontains(s[“name”], “Public-FW-ingress-egress”)], 1)
