In my previous blog post: Add SSL Certificate to Aviatrix Controller, we went through how to obtain a free public SSL certificate using ZeroSSL. It got great interface and you can get up to three 90 days certificate for free, but have following drawbacks:
- If you have two expired certificate, it counts as part of total three free 90 days certificate, and now you can only get one more.
- It does take a bit tickling to get a full chain certificate using commands.
Then I was introduced Posh-ACME, a PowerShell module to request and obtain free SSL certificates, let’s take a look how it works.
Pre-requisites:
- You own public DNS name and have ability to make DNS changes
- PowerShell installed. I personally recommend PowerShell Core, as it’s cross platform and Microsoft is actively developing on it. Follow the link for installation instruction.
- Posh-ACME module installed in PowerShell. Follow the link for installation instruction. Note the warning for PowerShell 5.1 or earlier.
To Request a certificate:
New-PACertificate <full.domain.name> -AcceptTOSOnce you issued the command, it will ask you to create an TXT record in your DNS domain: _acme-challenge.<full.domain.name>
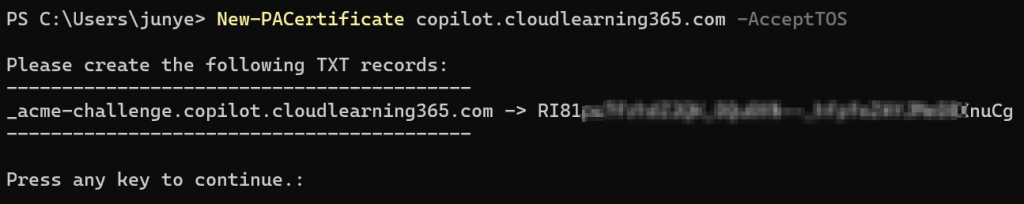
Example of the TXT record created in my DNS server
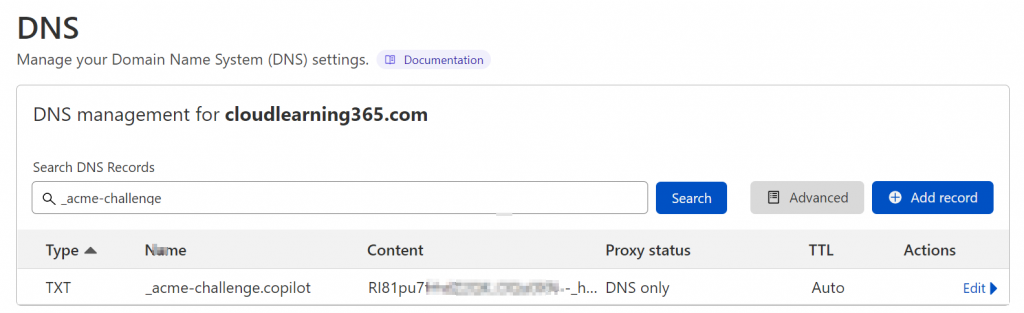
Note: After the TXT record has been created, I would wait for half an hour to make sure it’s fully replicated before go back to the command to press any key to continue, or you may have to do it over again.
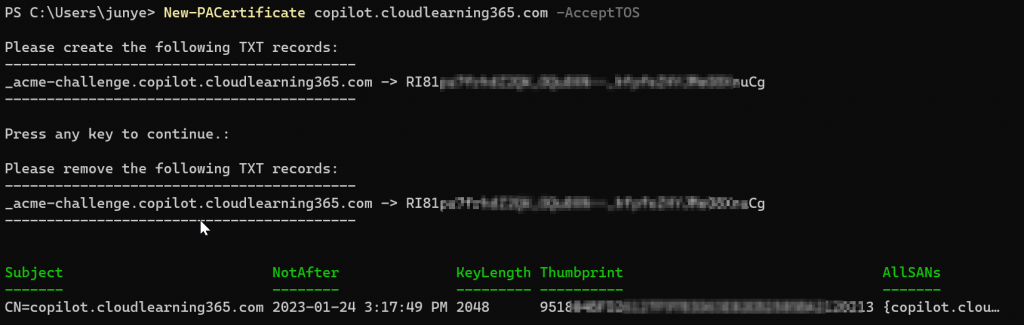
After you pressed any key, it could take a while, then you can see an certificate been issued with the full.domain.name you requested as the subject. Also it will recommend you to remove the TXT record.
To view the issued certificates, run
Get-PACertificate | flYou can see it will tell you the path where the certificates are stored. Also have different type of certificates prepared for you already.
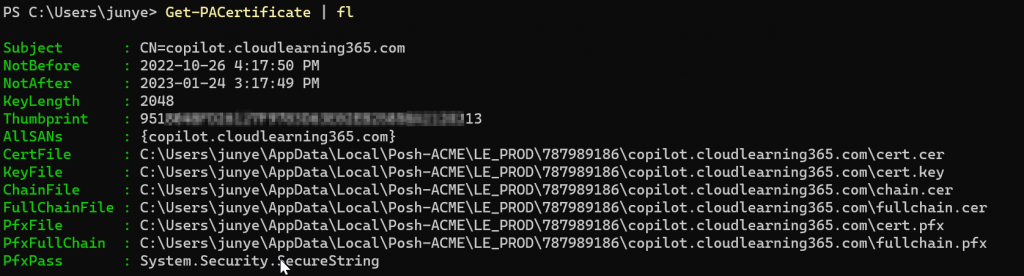
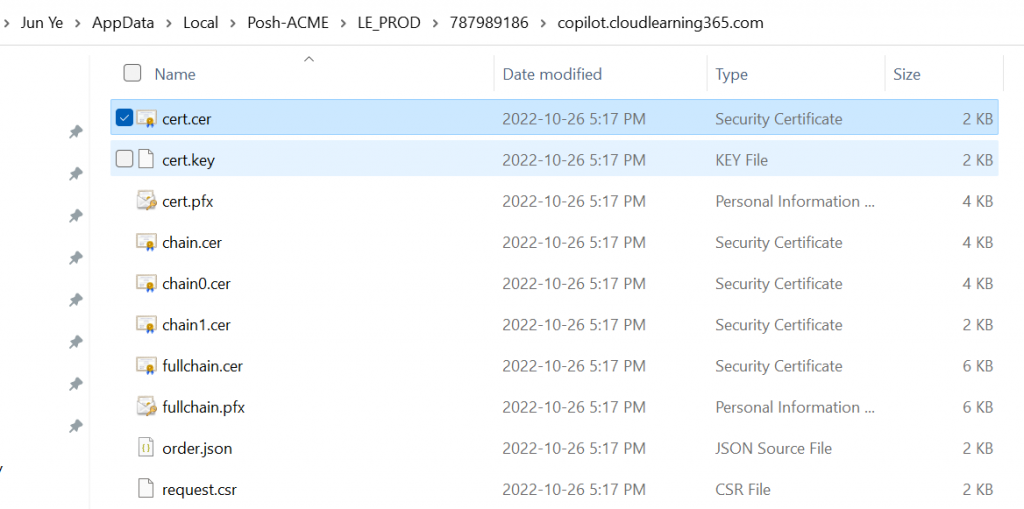
You can simply start to use the certificates based on the requirements:
cert.cer (Base64 encoded PEM certificate)
cert.key (Base64 encoded PEM private key)
cert.pfx (PKCS12 container with cert+key)
chain.cer (Base64 encoded PEM with the issuing CA chain)
chainX.cer (Base64 encoded PEM with alternate issuing CA chains)
fullchain.cer (Base64 encoded PEM with cert+chain)
fullchain.pfx (PKCS12 container with cert+key+chain)Note: the .pfx file password is: poshacme
