In AWS, subnet that doesn’t have default 0.0.0.0/0 point to Internet Gateway (IGW) is considered as private subnet. Where subnet that have default 0.0.0.0/0 point to IGW is considered as public subnet. Instances running on private subnet still need to access Internet to download patches, packages etc. You may use AWS NAT Gateway on public subnet to provide this connectivity. NAT Gateway cost $0.045 USD per hour plus $0.045 per GB data processed.
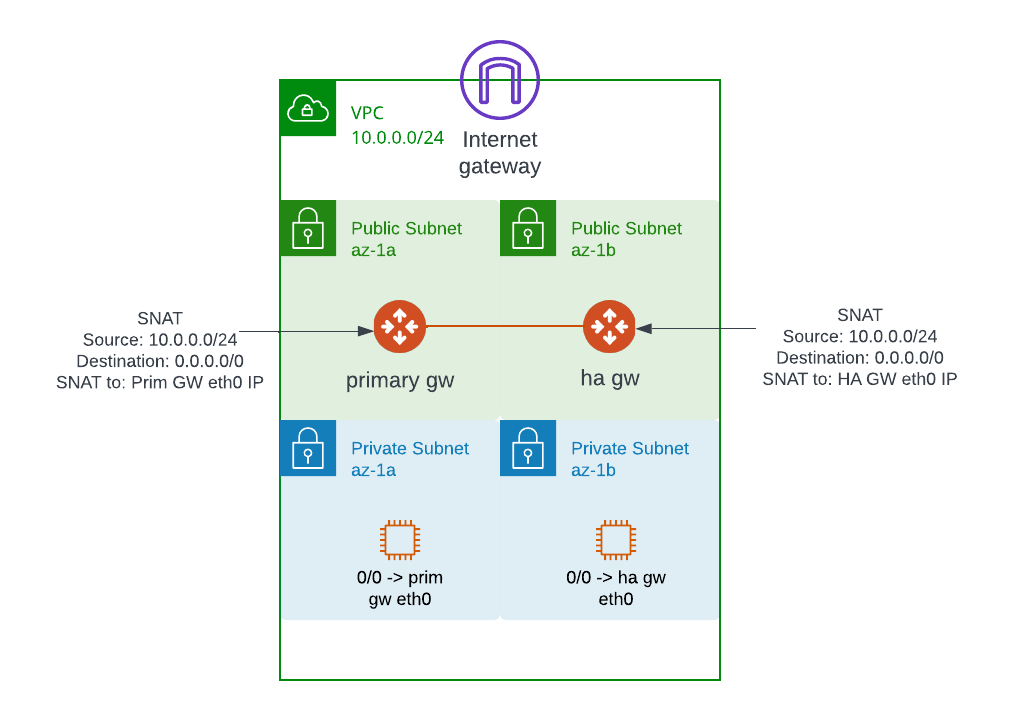
If you already have Aviatrix Spoke Gateway deployed, and need internet access (egress) from private subnet, also you don’t need any fancy egress control, then you may reuse the existing Aviatrix Spoke Gateway as Egress Gateway by using SNAT rule.
If you need better control and traffic inspection, you should consider Aviatrix FQDN egress gateway for L7 egress control based on Fully Qualified Domain Name eg: allow https://github.com deny https://youtube.com. Or if deep packet inspection using Next Generation Firewall (NGFW) is required, then you may consider Aviatrix FireNet with NGFW integration.
Simple diagram:
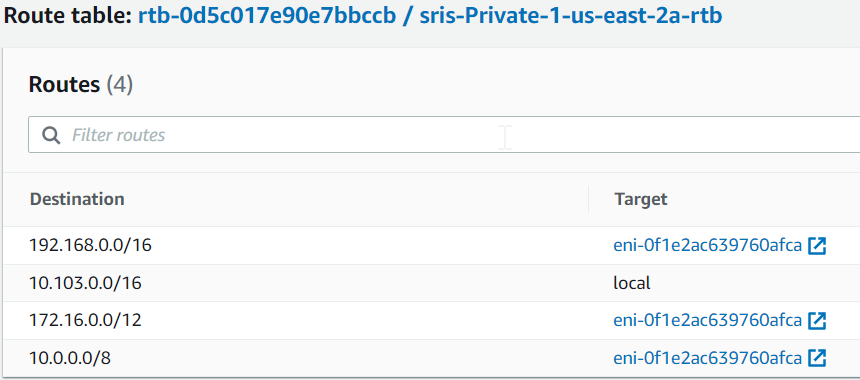
Following is a typical private subnet that managed by Aviatrix, where Aviatrix insert RFC1918 routes, 10.0.0.0/8, 172.16.0.0/12 and 192.168.0.0/16 into private subnet route table and point them to Aviatrix Spoke Gateway eth0 interface
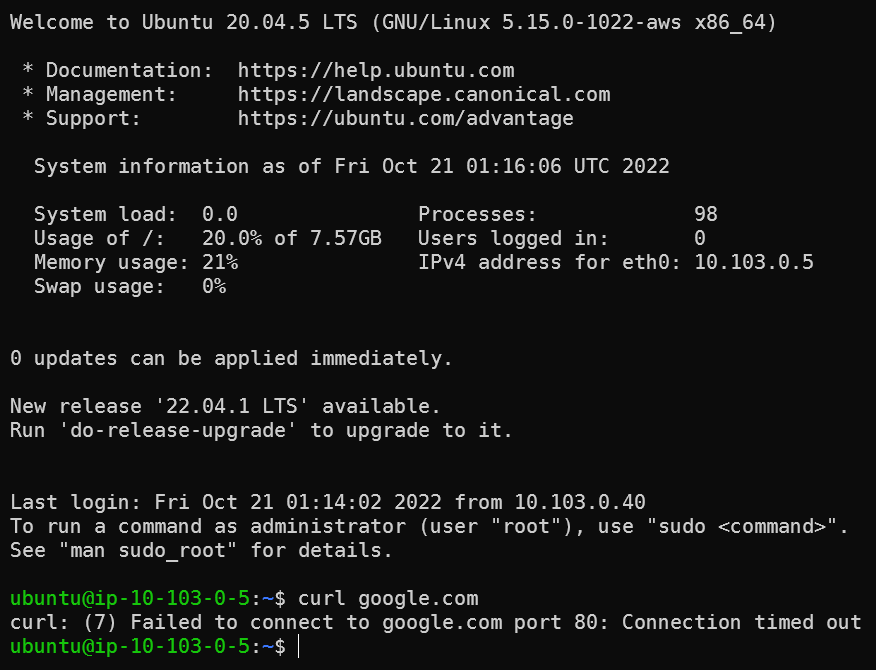
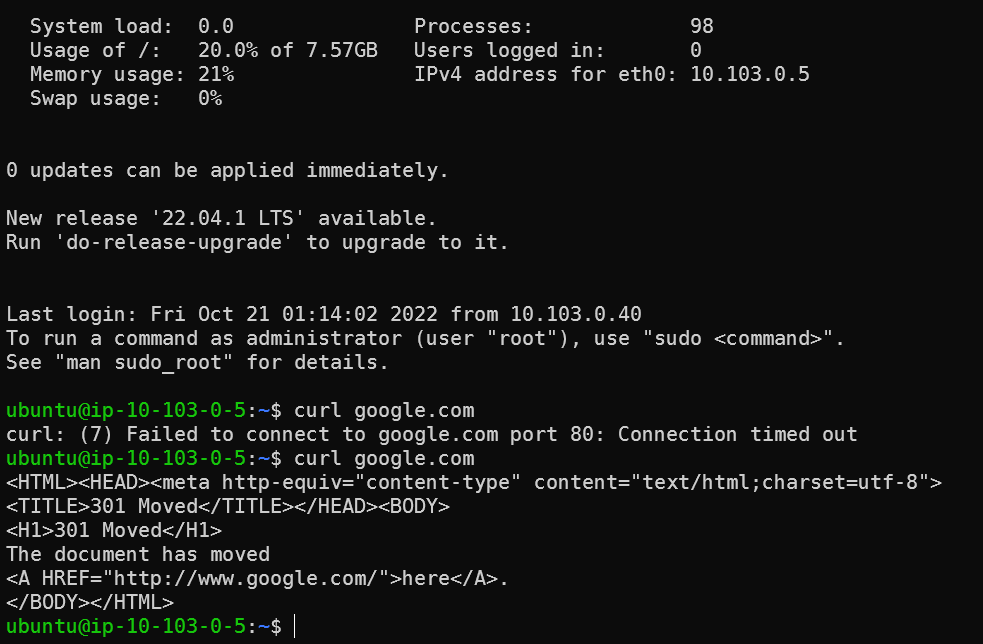
Try to access google.com from the private instance, getting connection timed out:
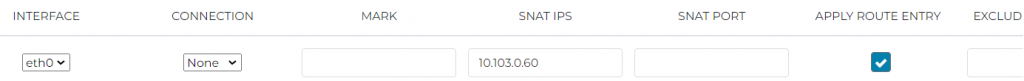
To add SNAT rule to the Spoke Gateway, go to Aviatrix Controller -> Gateways -> Find the spoke gateway, then click on EDIT (If you have HA gateway, you will need to complete this same step on the -hagw as well)
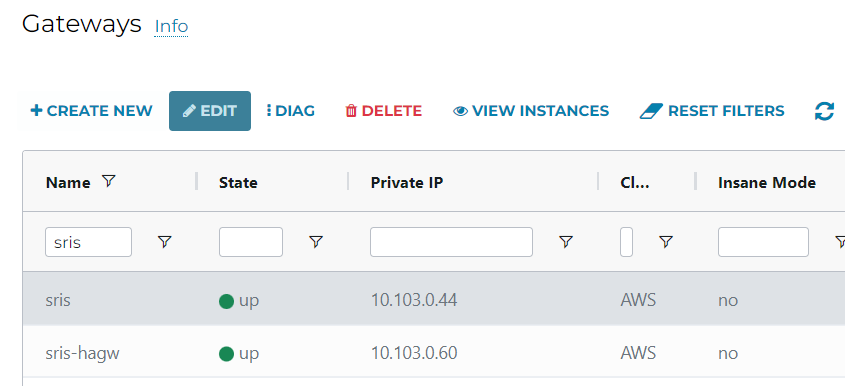
Scroll to Source NAT section, select Customized SNAT, make sure Sync to HA Gateway isn’t selected.
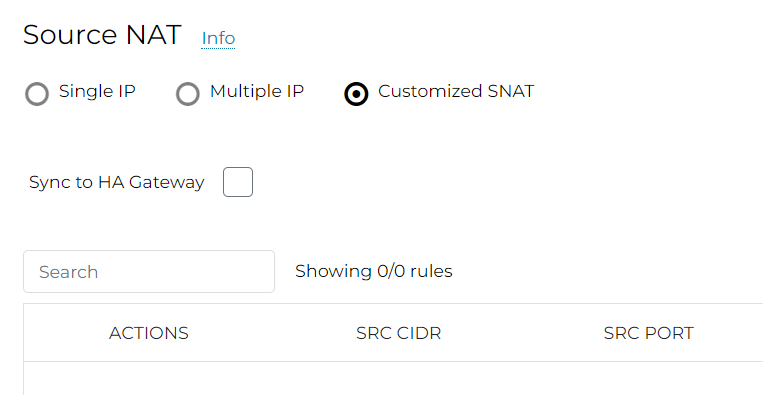
Click on ADD NEW
- SRC CIDR : Local VPC’s CIDR, this is where the traffic would be originated
- DST CIDR: Enter 0.0.0.0/0 as that’s where anything we don’t locally have, hence Internet
- INTERFACE: Traffic will be seen going out from Spoke Gateway’s eth0 interface
- SNAT IPS: Since Traffic will be seen going out from Spoke Gateway’s eth0 interface, we need it’s eth0 interface IP
- APPLY ROUTE ENTRY: Checked, with this Aviatrix will program VPC Route Table to add 0.0.0.0/0 point to Aviatrix Spoke Gateway
- EXCLUDE ROUTE TABLE: If you don’t want any specific Route Table to apply the 0.0.0.0/0 route, then enter the name of the Route Table here.
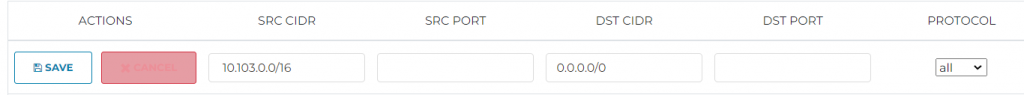
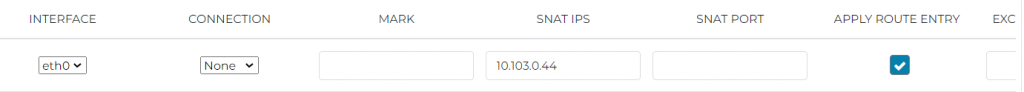
After this is done remember to scroll to left and click on SAVE
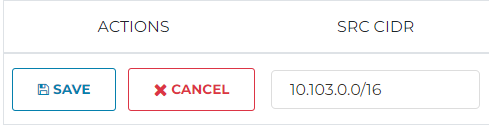
Also remember to click on UPDATE once the rule is saved to commit the change to the Spoke Gateway.

You will be prompted to confirm customized SNAT rule:
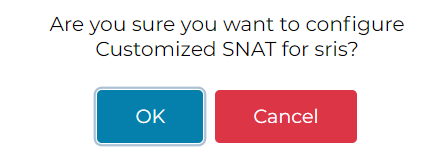
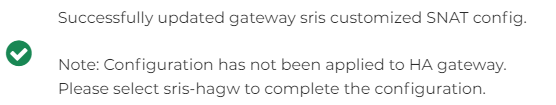
If you have HA Gateway, repeat above steps, but this time set up the SNAT rule on HA Gateway, and the SNAT IP would be HA Gateway’s eth0 IP
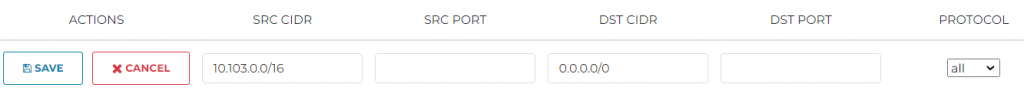
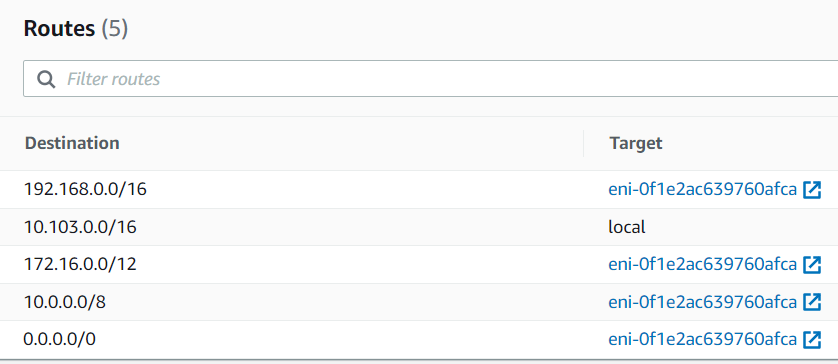
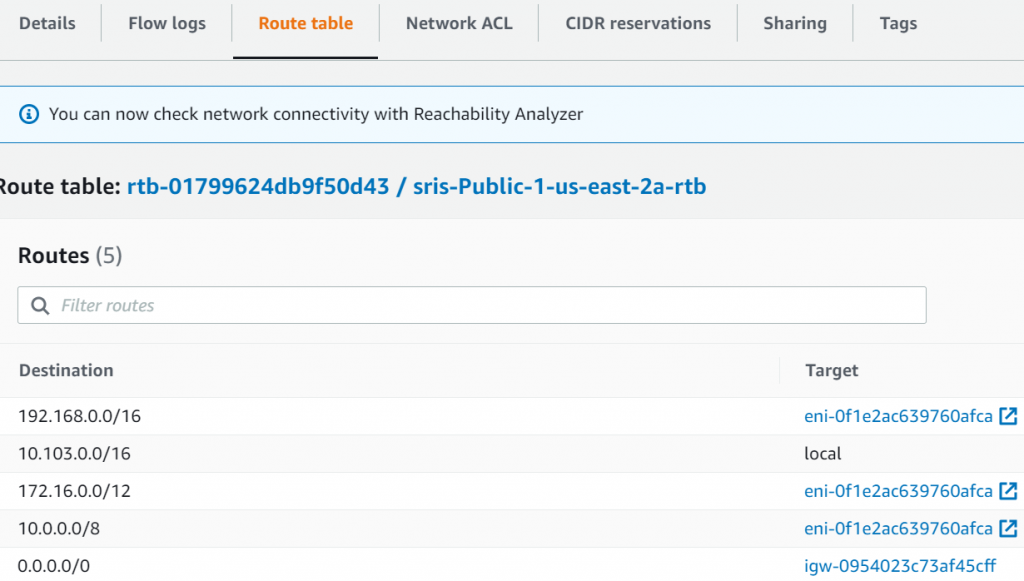
After this is done, refresh the private subnet route table, you can see 0.0.0.0/0 gets added point to Spoke Gateway’s interface
Test again from the private instance, now we are getting response back.
How does it work?
Here’s a great NAT Processing Order diagram inspired from Barry Li
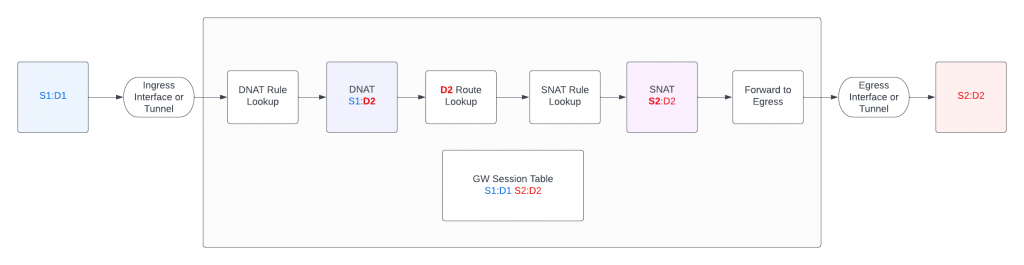
- Aviatrix Spoke Gateway receives client 10.103.0.5 destination to google from eth0
- There’s no DNAT rule apply, goes to routing decision, which will be send to subnet 10.103.0.32/28 default gateway 10.103.0.33 via eth0
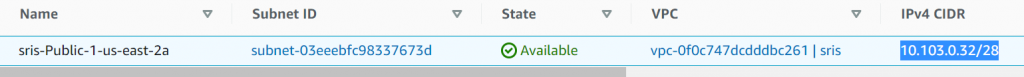
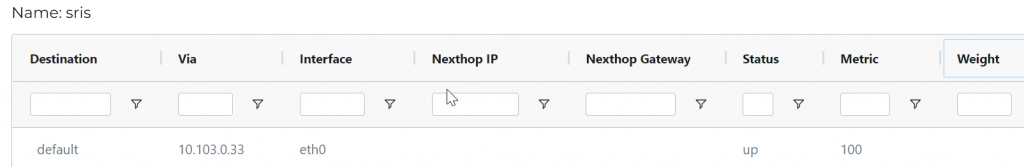
- Once the routing decision has been made, SNAT rule comes in and replaced 10.103.0.5 with Spoke Gateway eth0 IP: 10.103.0.44, then leaves eth0 to AWS fabric towards subnet default gateway 10.103.0.33
- Subnet route table tell the traffic would follow 0.0.0.0/0 via IGW, then send to internet.
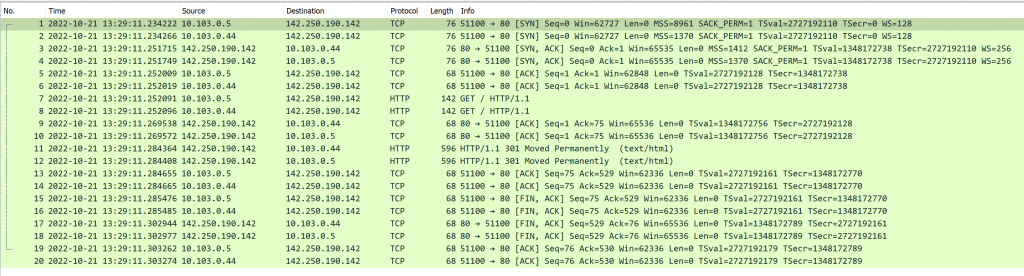
Packet capture on the spoke gateway, when curl google.com is happening
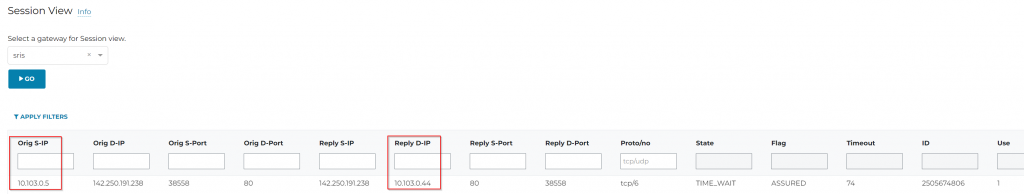
10.103.0.5 is the private subnet client
10.10.0.44 is the Spoke Gateway
Session view on the spoke way also shows the NAT translation.