This blog serves as a guide to configure GCP Interconnect, Cloud Router to form an BGP session with on-premise BGP capable devices. With VPC peering and import and export routes on the peering, it’s possible to connect up to 25 spoke VPCs to the interconnect VPC.
GCP Console
In order to set up the Interconnect, you must first create a VPC that will serve as the landing point for the Interconnect Cloud Router.
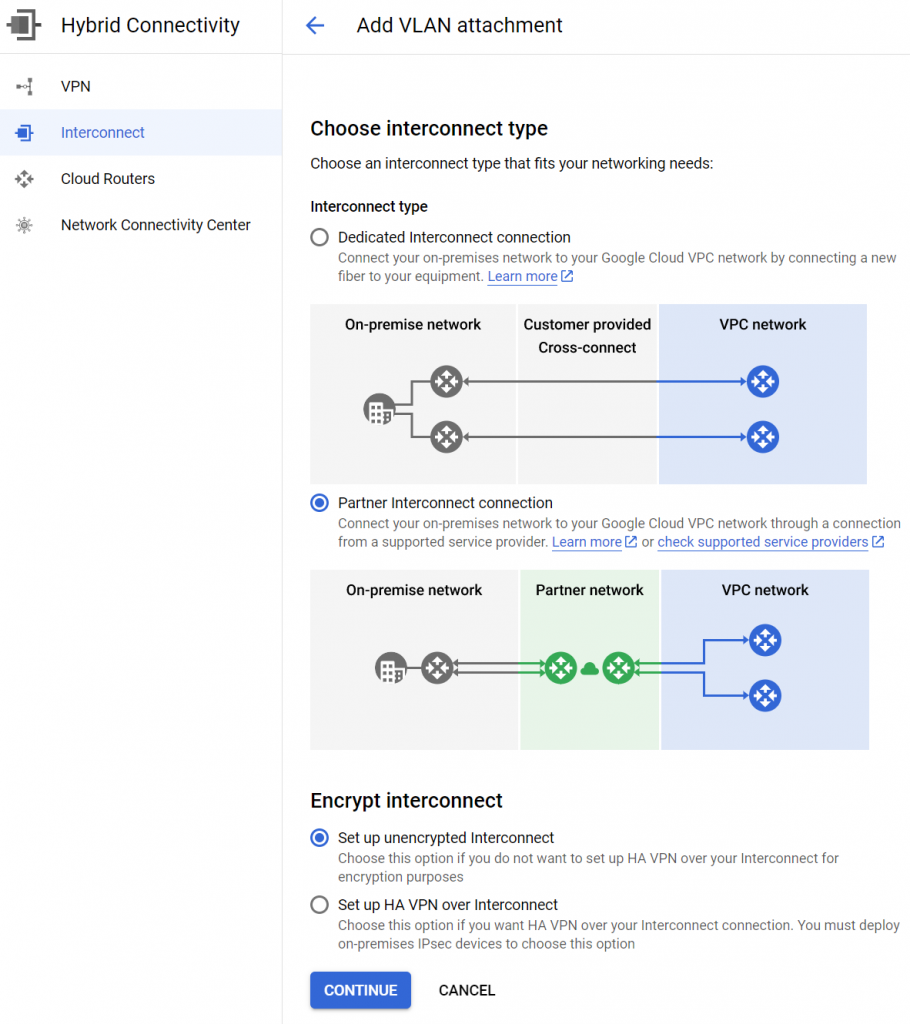
Under Hybrid Connectivity, try to create Interconnect. Following example shows VLAN attachment:
Chose Partner Interconnect connection
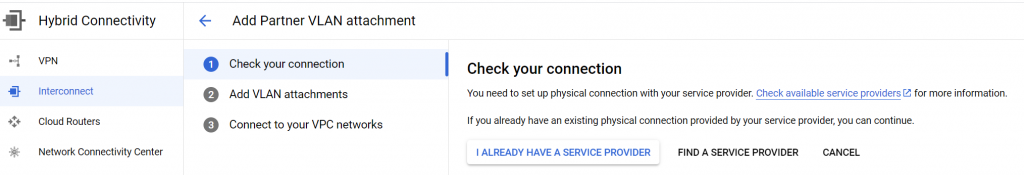
We already have a service provider Equinix
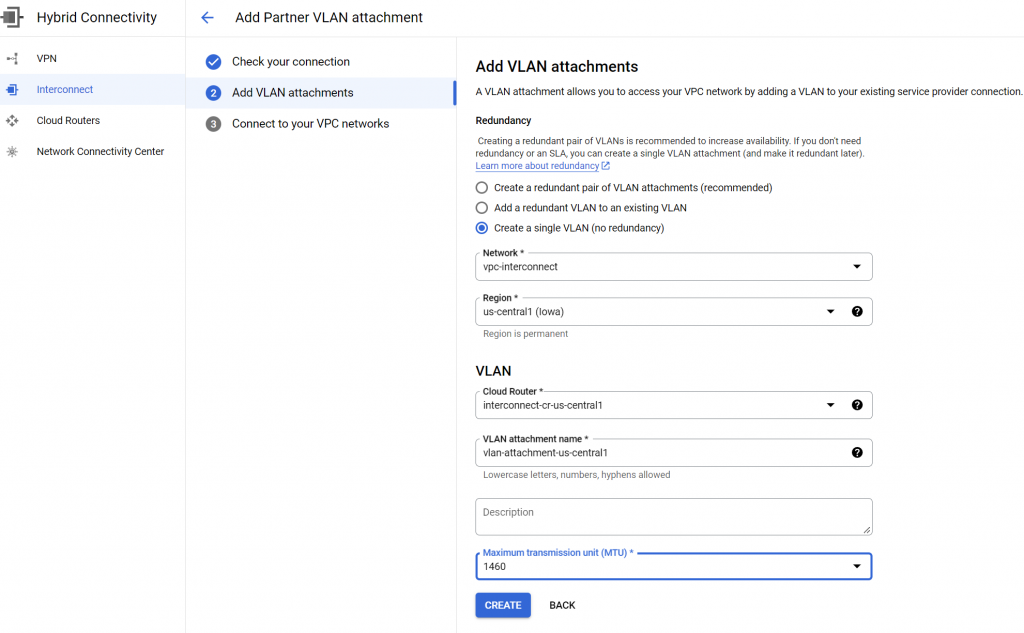
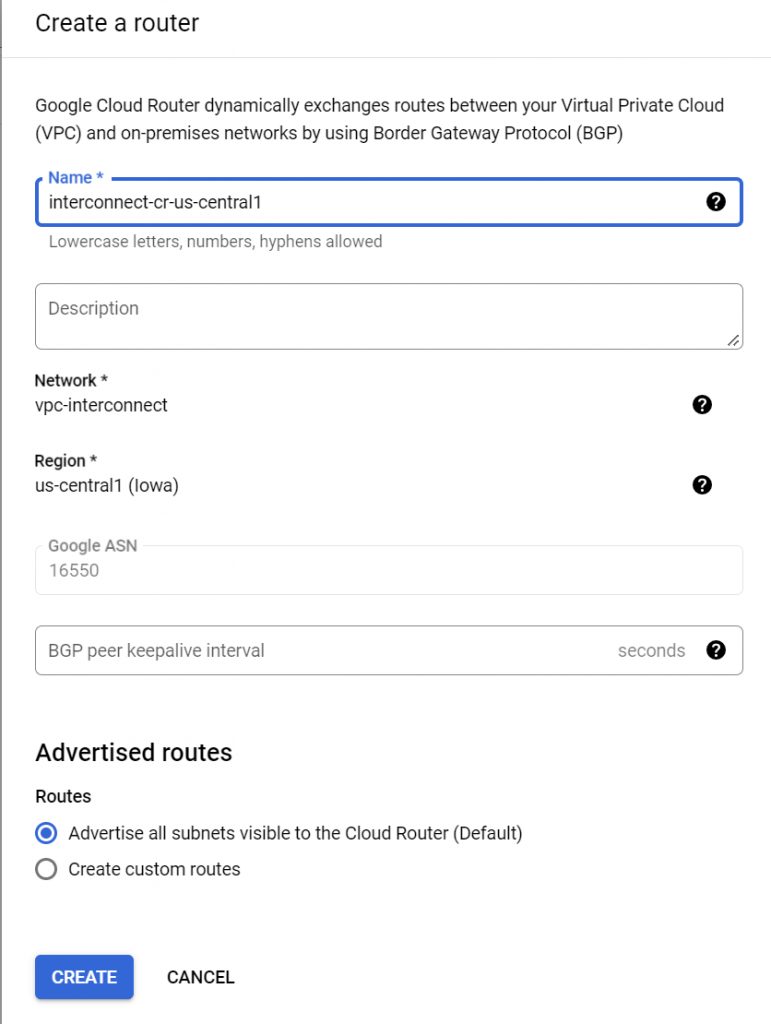
Create a Cloud Router for the VLAN attachment
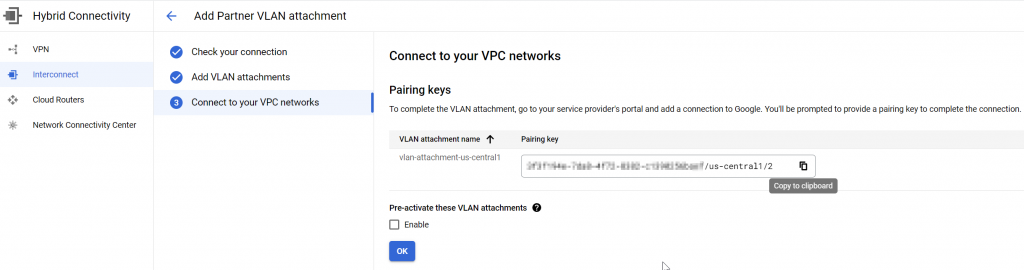
Obtain the VLAN attachment pairing key
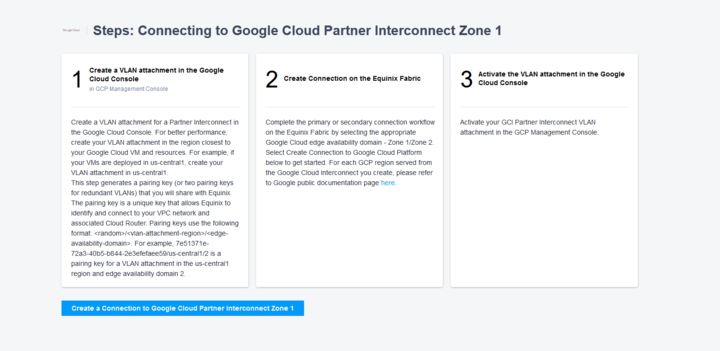
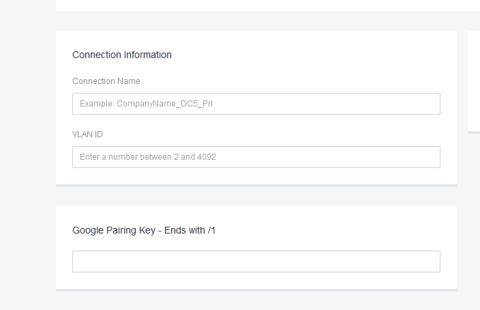
Service provider side – Equinix shown below
Back to GCP console
The attachment is now waiting for activation
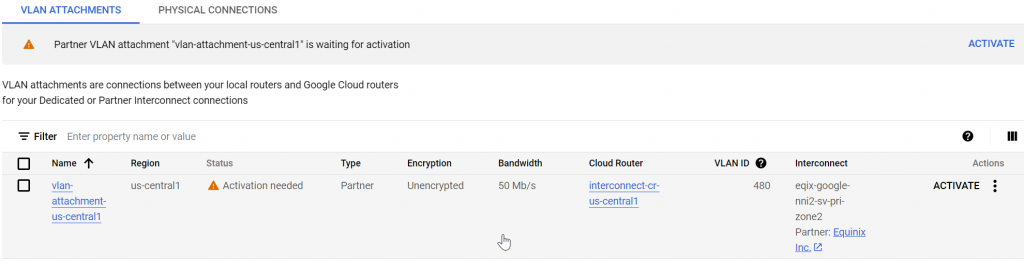
After click on Activate

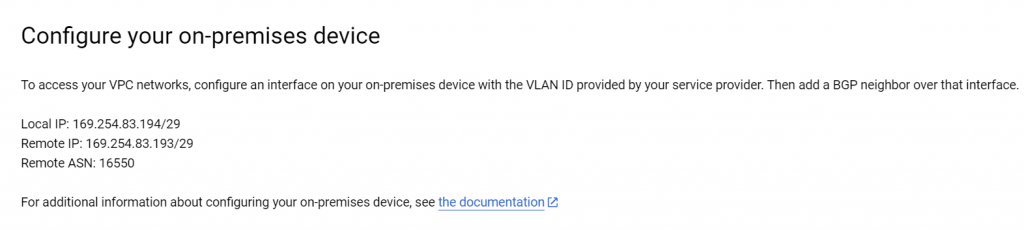
Now we need to configure BGP with customer side router
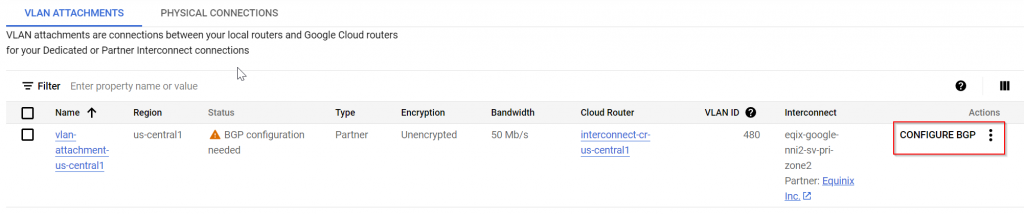
Enter on-prem router BGP ASN and note down BGP IPs
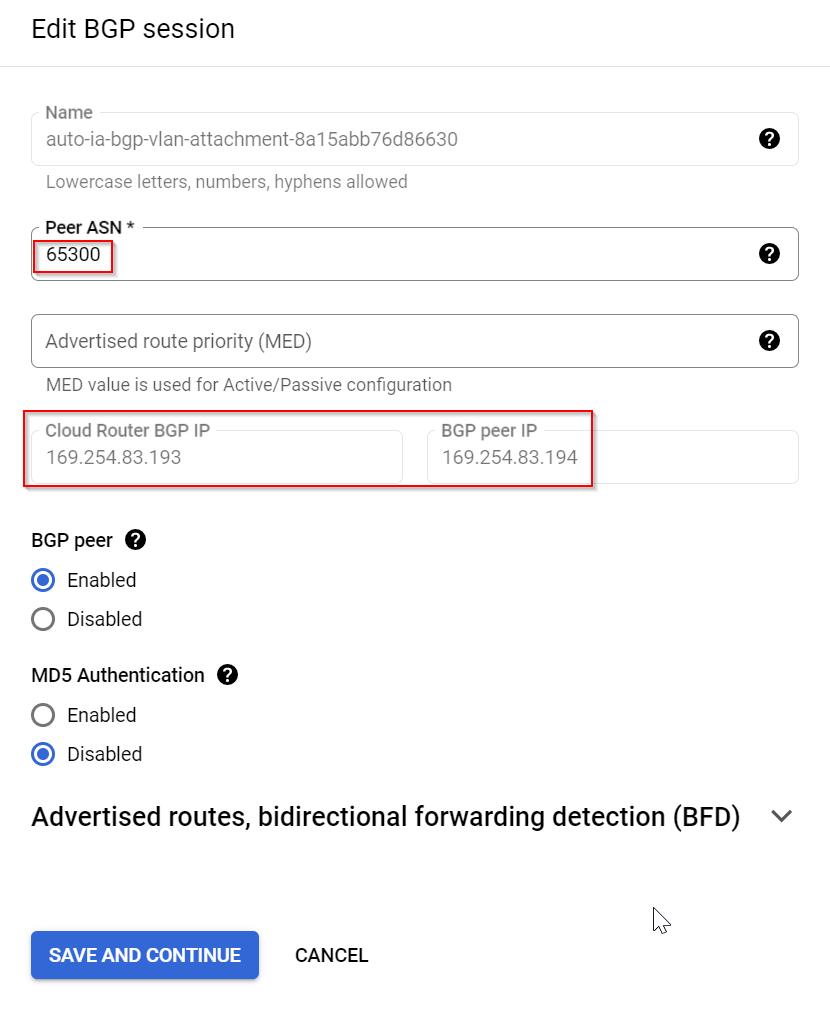
It doesn’t provide the mask of the BGP IP, also makes no mention of the Cloud Router ASN
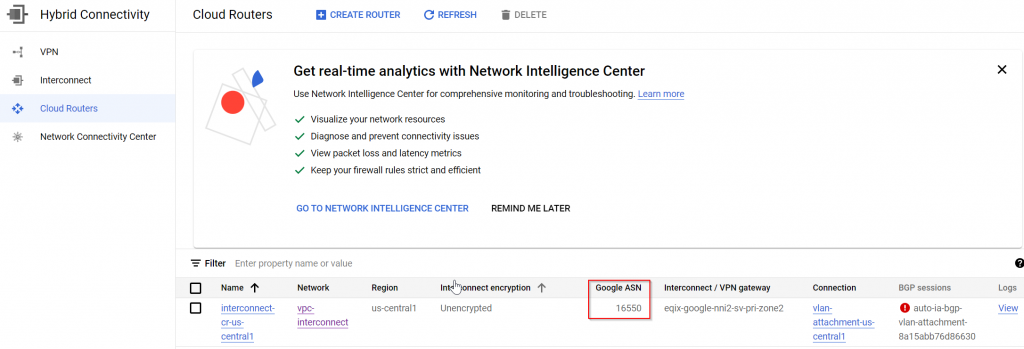
You may obtain Cloud Router ASN number for the Interconnect:
Or click on Troubleshoot on the VLAN attachment
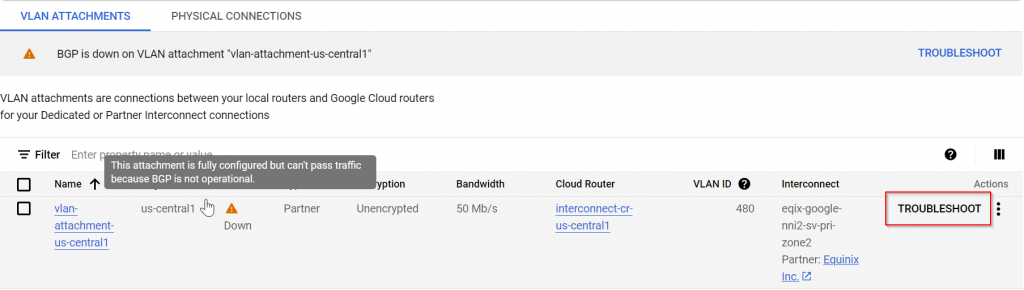
There, much more straightforward, just a catch: Local means on-prem router, remote means Cloud Router in this sentence.
Configure ISR for the VLAN interface and confirm L2 connecitivy
ISR-2(config)#interface GigabitEthernet0/0.832
ISR-2(config-subif)#
ISR-2(config-subif)#ip address 169.254.83.194 255.255.255.248
ISR-2(config-subif)#end
ISR-2#ping 169.254.83.193 source 169.254.83.194
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 169.254.83.193, timeout is 2 seconds:
Packet sent with a source address of 169.254.83.194
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 40/40/44 ms
Configure BGP
ISR-2(config)#router bgp 65300
ISR-2(config-router)#neighbor 169.254.83.193 remote-as 16550
ISR-2(config-router)#end
Check BGP status
ISR-2#show ip bgp summary
BGP router identifier 10.1.88.88, local AS number 65300
BGP table version is 8, main routing table version 8
1 network entries using 140 bytes of memory
1 path entries using 56 bytes of memory
1/1 BGP path/bestpath attribute entries using 128 bytes of memory
1 BGP extended community entries using 24 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 348 total bytes of memory
BGP activity 105/103 prefixes, 164/162 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
169.254.83.193 4 16550 10 14 8 0 0 00:02:53 0
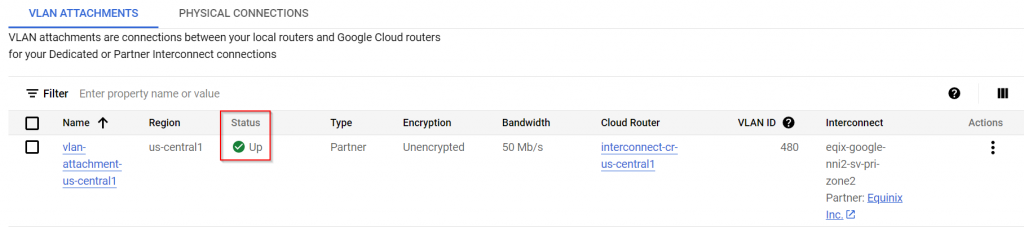
The VLAN attachment shows up on GCP console
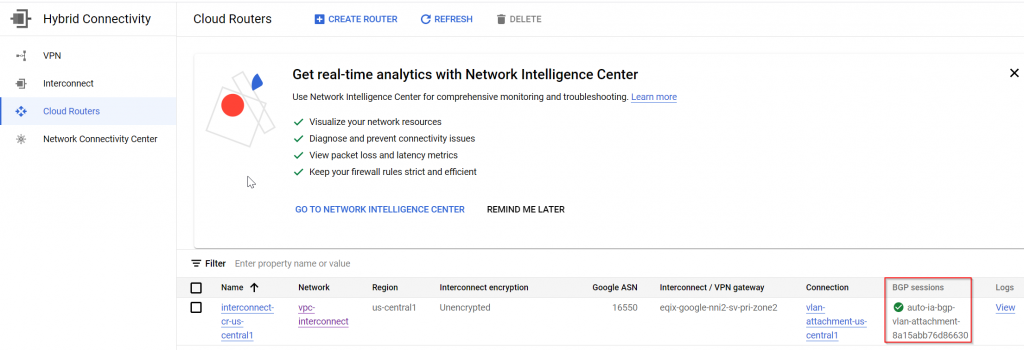
Cloud Router also shows BGP session up
On-prem router is advertising 10.1.13.0/24:
router bgp 65300
bgp log-neighbor-changes
neighbor 169.254.83.193 remote-as 16550
!
address-family ipv4
network 10.1.13.0 mask 255.255.255.0
neighbor 169.254.83.193 activate
exit-address-familySwitch back to the interconnect VPC, note it doesn’t have any subnet yet
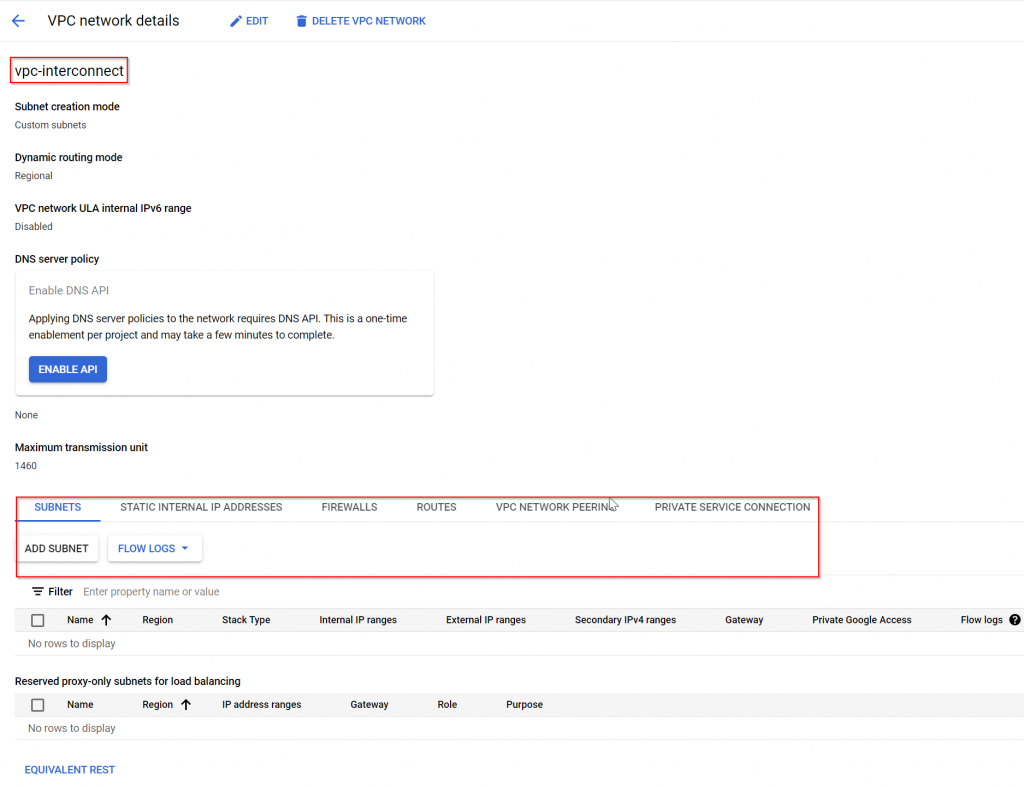
Exam route table of interconnect VPC, we can observe the advertised route from on-prem
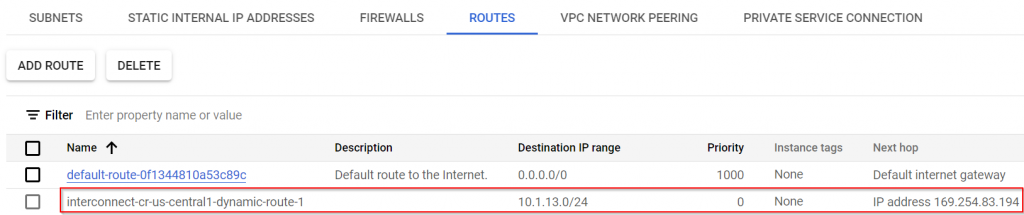
On the ISR side, now we only see local route
ISR-2#show ip bgp
BGP table version is 8, local router ID is 10.1.88.88
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external, f RT-Filter
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 10.1.13.0/24 0.0.0.0 0 32768 i
Try to add a subnet to the interconnect VPC: (NOTE, this subnet isn’t required for the Interconnect to work, but with it we can see the CIDR of the subnet gets advertised to on-prem via Cloud Router by default.)
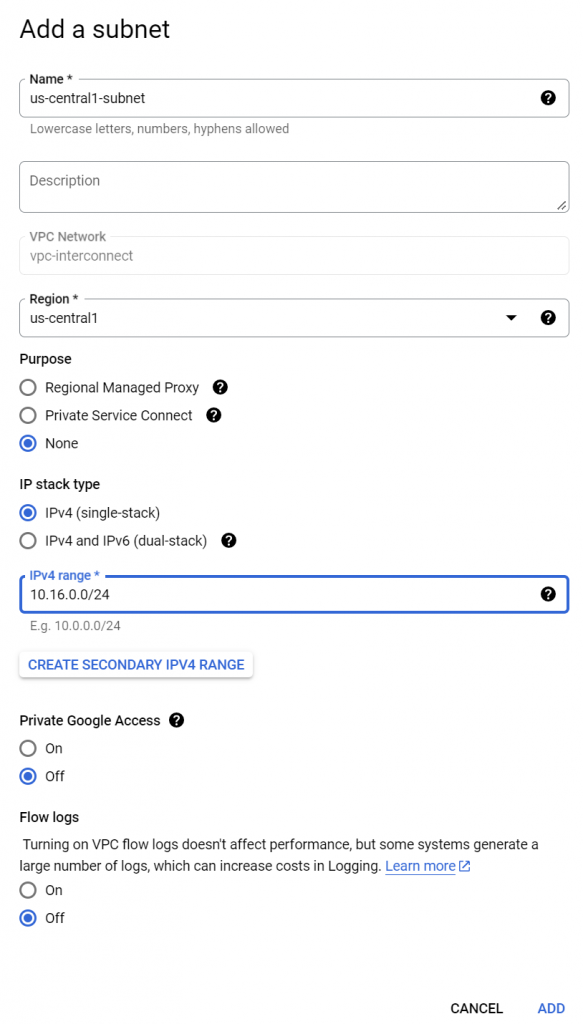
Now check on-prem router, and it does indeed received the added subnet prefix from Cloud Router:
ISR-2#show ip bgp
BGP table version is 9, local router ID is 10.1.88.88
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external, f RT-Filter
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 10.1.13.0/24 0.0.0.0 0 32768 i
*> 10.16.0.0/24 169.254.83.193 100 0 16550 ?
If you edit the cloud router, you can see the default setting is to Advertise all subnets visible to the Cloud Router
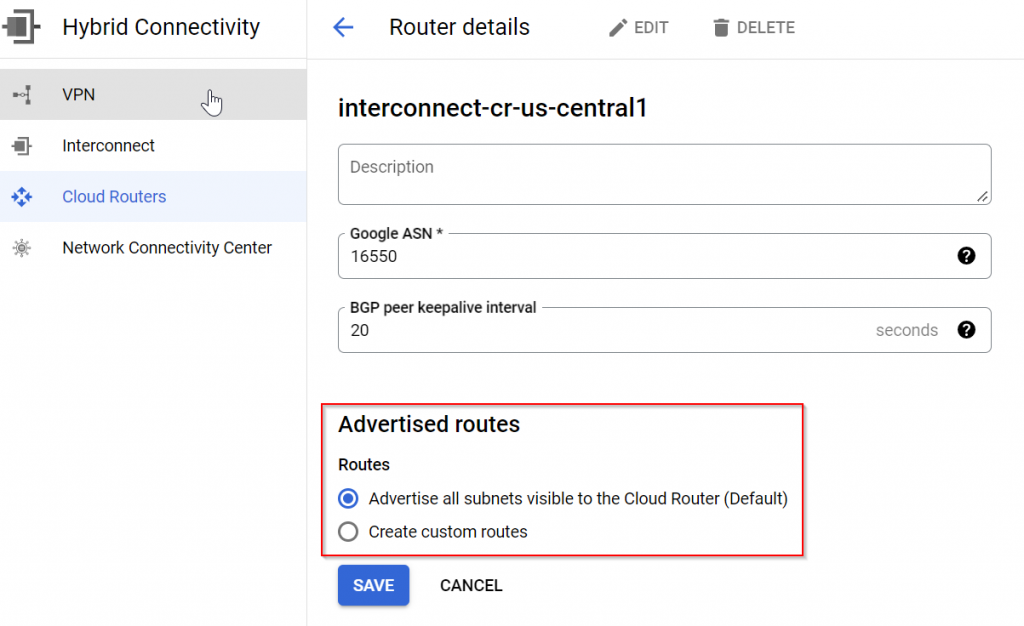
To test how Cloud Router propagate routes, let’s create a spoke VPC, also with no subnets.
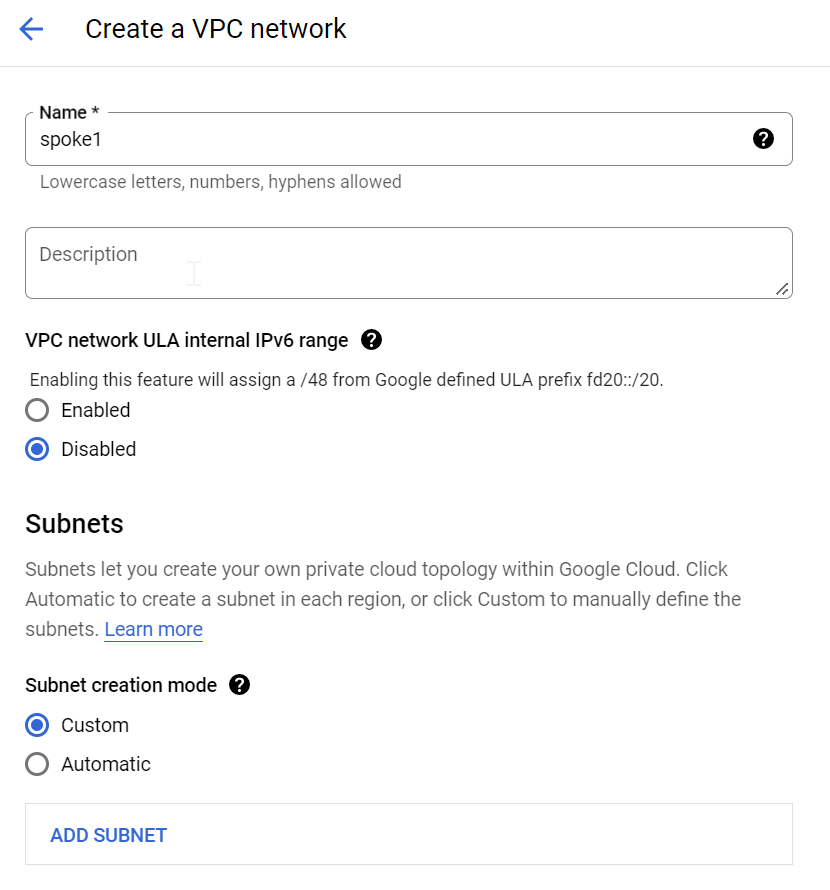
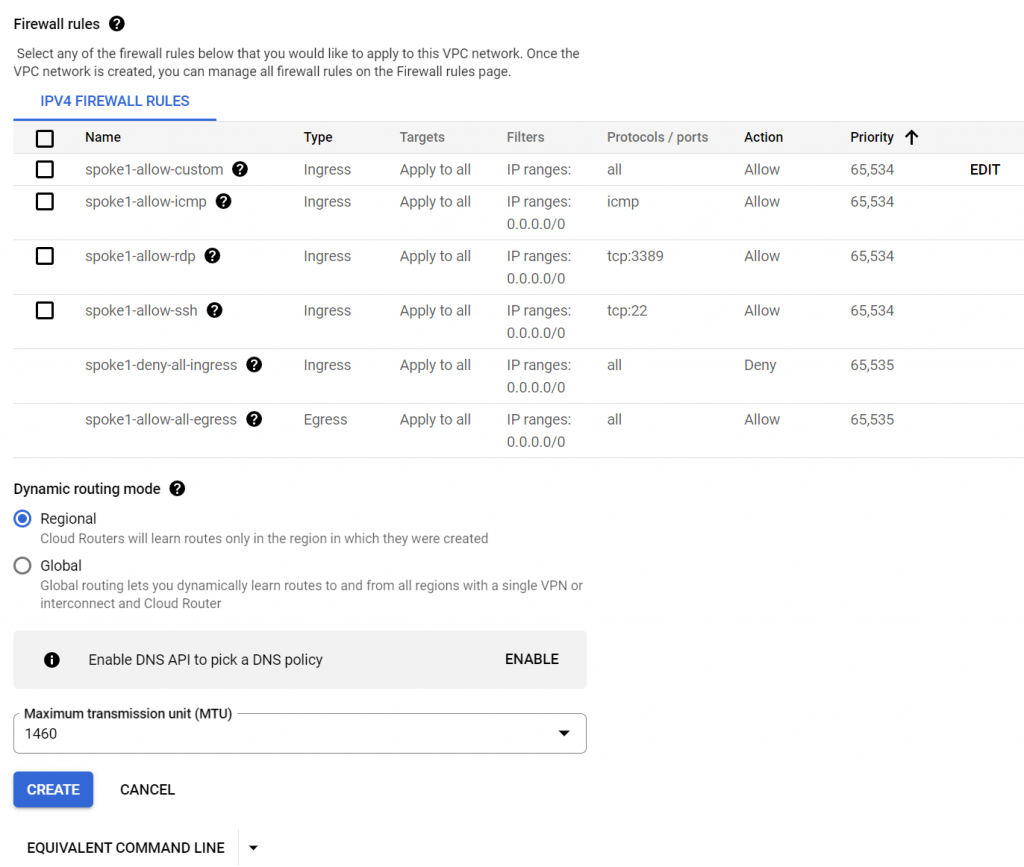
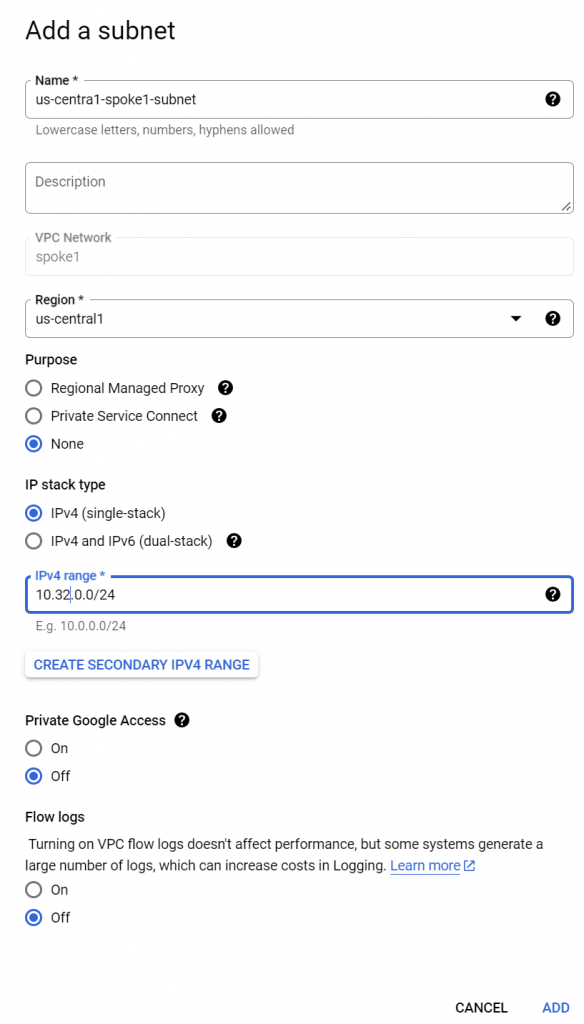
Add a subnet to spoke1
Peer this spoke1 VPC with interconnect VPC, and check import/export routes
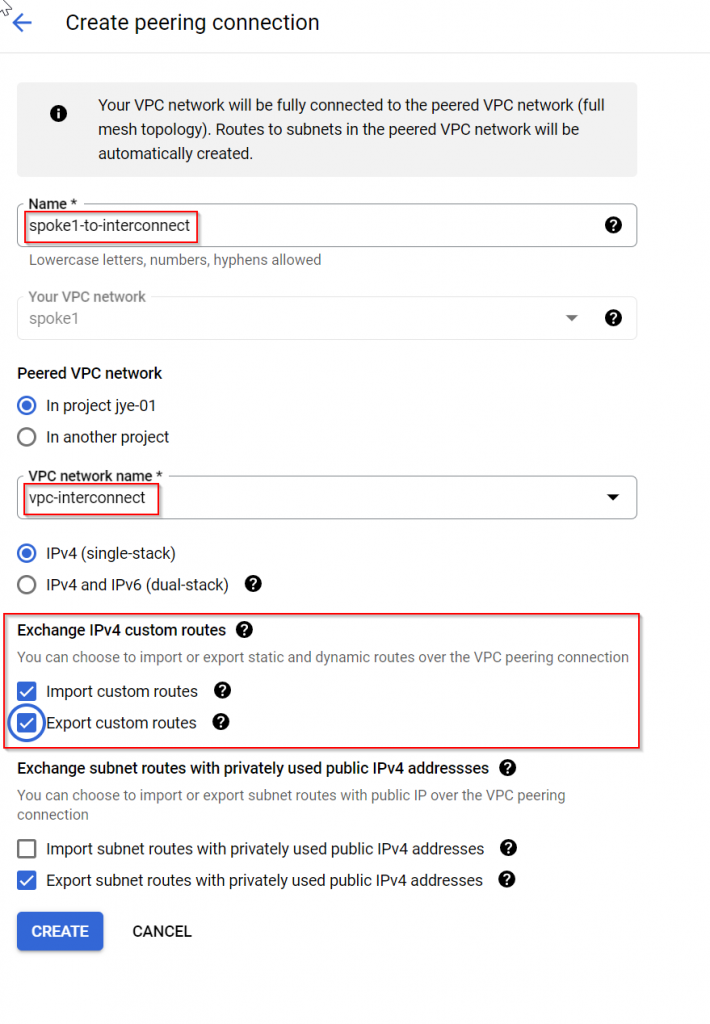
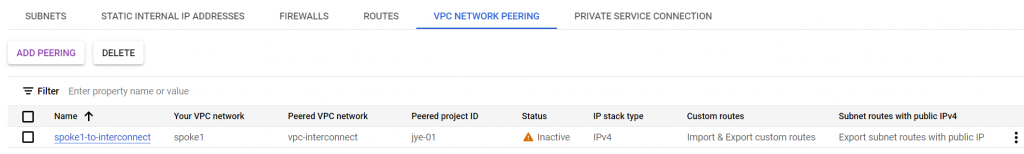
The peering status shows as inactive, need to create peering from interconnect VPC towards spoke1 VPC
Create peering from interconnect VPC to spoke1, also enable import/export routes
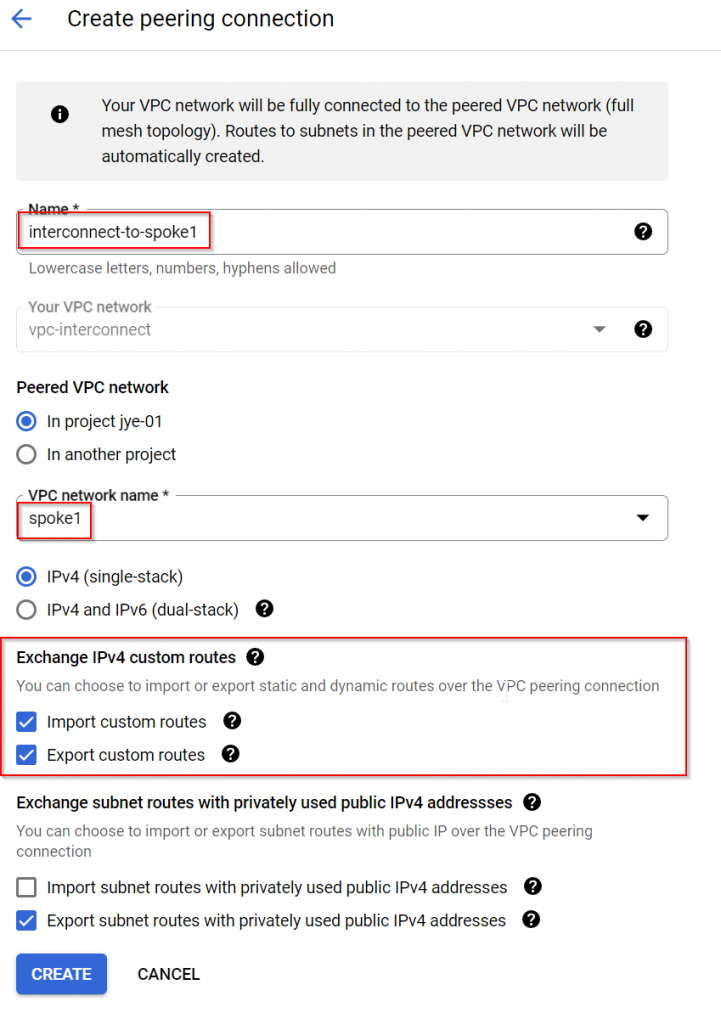
Now the peering from both sides are active
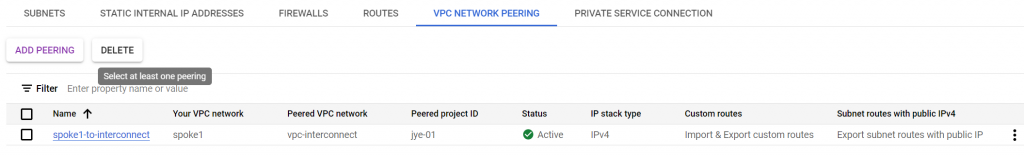
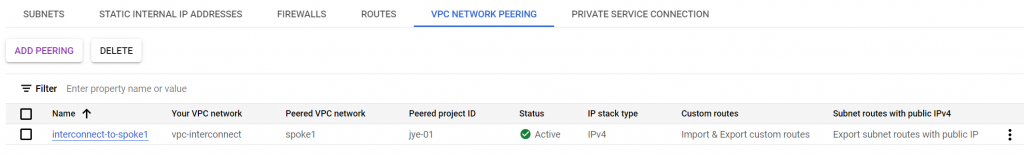
Check spoke1 route table, it learned route 10.16.0.0/24 to interconnect VPC. But we don’t see on-prem route 10.113.0/24 via interconnect VPC. Notice the banner explained that imported custom dynamic routes are omitted from the list.
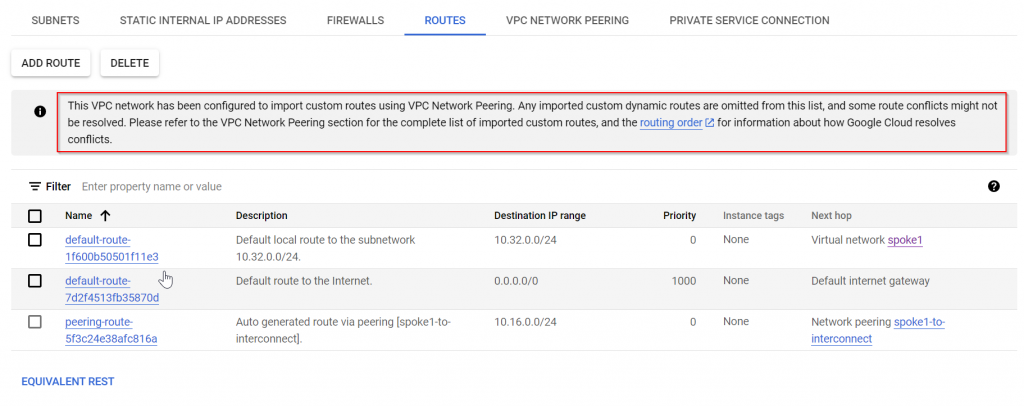
To see the imported route, go to VPC peering -> Click on the peering connection
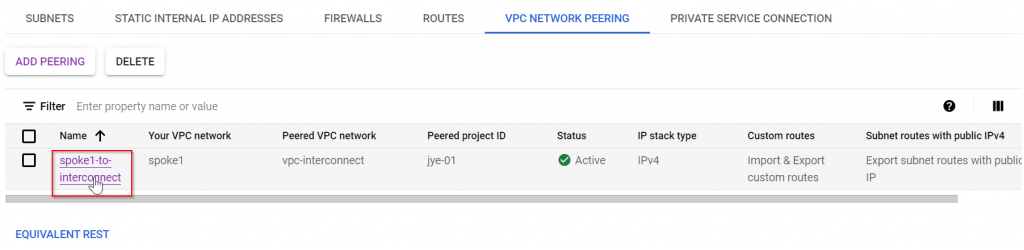
We can see 10.1.13.0/24 has been imported as dynamic peering route, and status is accepted. If there’s any conflict, the status will not be accepted.
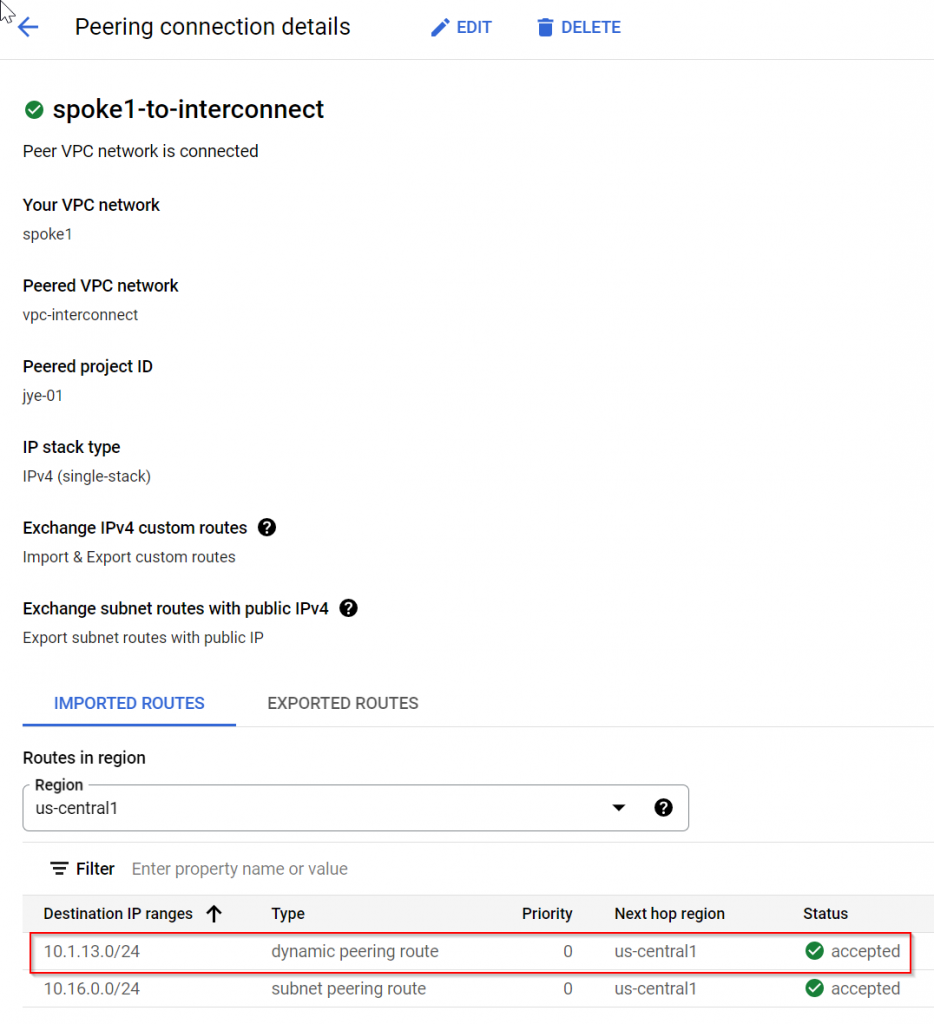
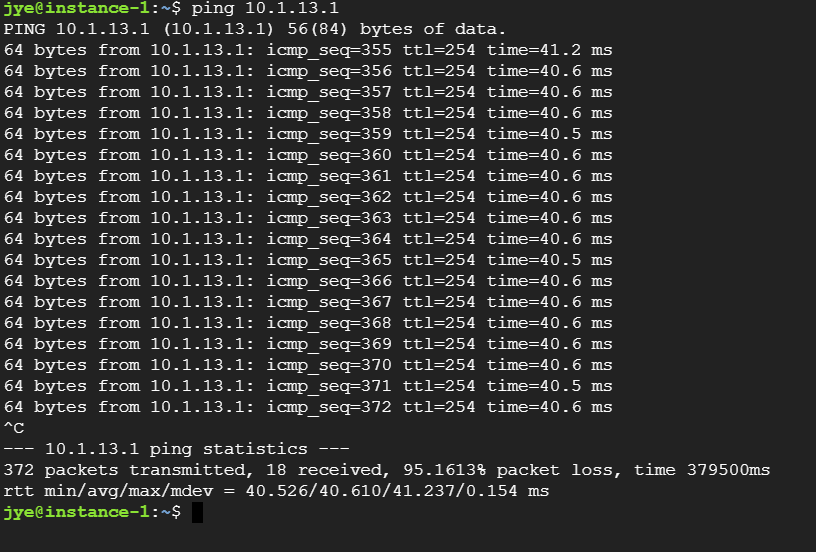
To test, deploy an instance in the spoke1 subnet and try to reach on-prem router 10.1.13.1
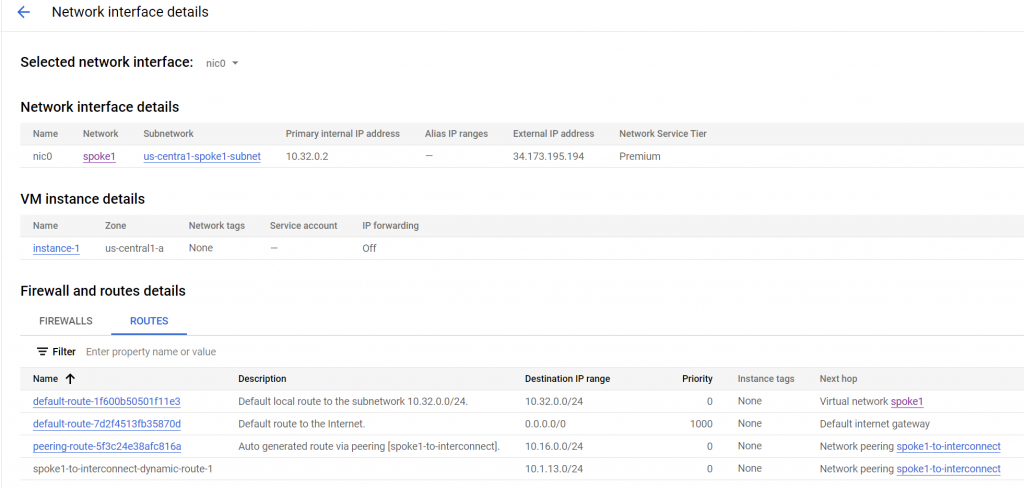
ping is failing, though the route to on-prem is there.
Check on-prem router routes, it only learned the interonnect VPC prefix 10.16.0.0/24, not the spoke1 VPC prefix 10.32.0.0/24
ISR-2#show ip bgp
BGP table version is 11, local router ID is 10.1.88.88
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external, f RT-Filter
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 10.1.13.0/24 0.0.0.0 0 32768 i
*> 10.16.0.0/24 169.254.83.193 100 0 16550 ?
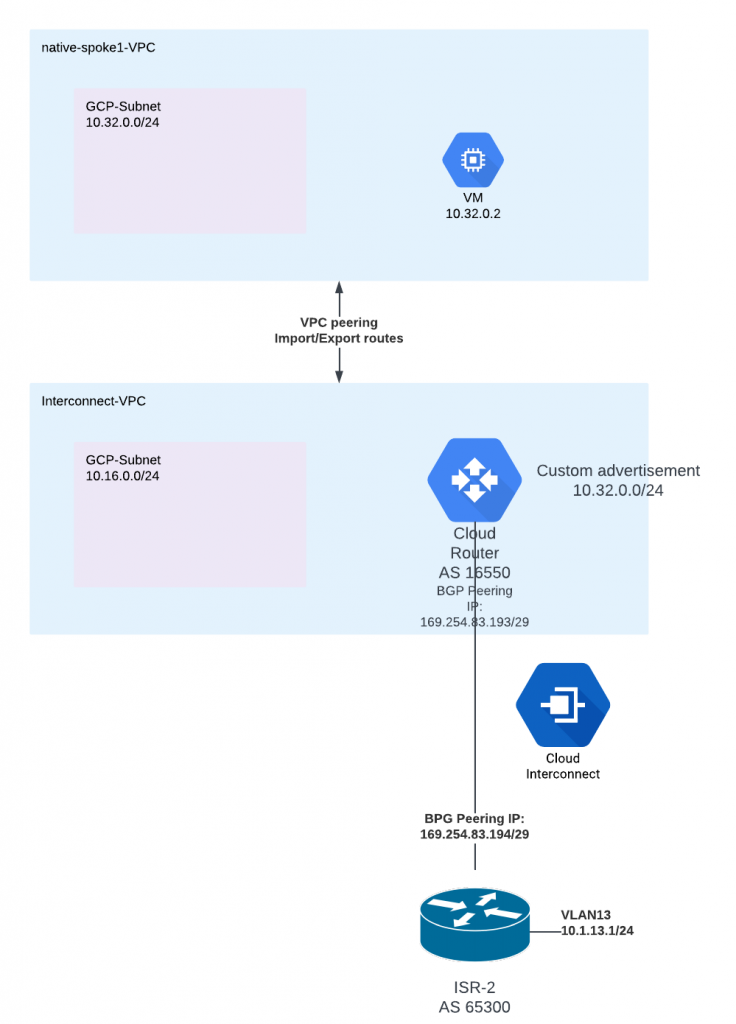
Remember Cloud Router is default to: Advertise all subnets visible to the Cloud Router. Currently Cloud Router only knows about the prefixes of the VPC it’s associated with. It’s not aware of prefixes coming from the VPC peering, as there’s no BGP connection. So we must use custom routes feature of the Cloud Router
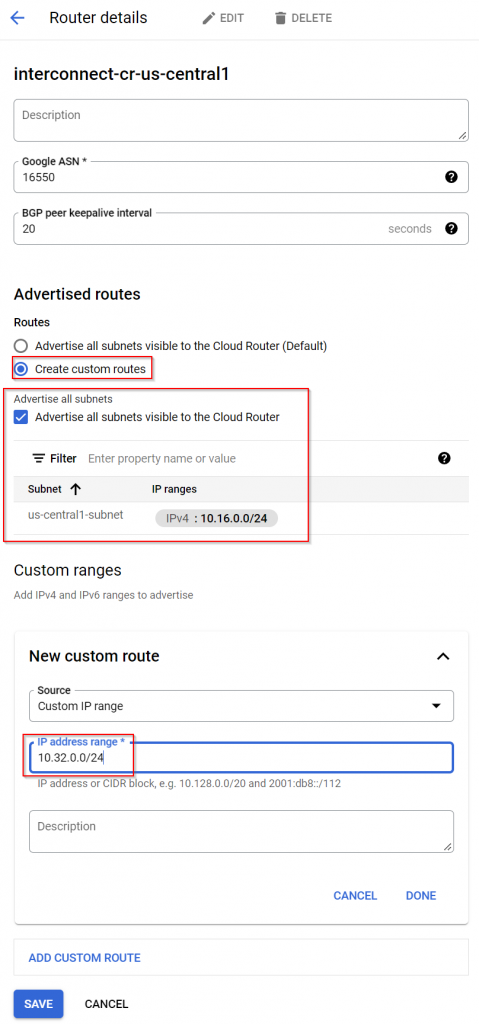
After this is done, on-prem router receives the spoke1 route from Cloud Router
ISR-2#show ip bgp
BGP table version is 12, local router ID is 10.1.88.88
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, x best-external, f RT-Filter
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 10.1.13.0/24 0.0.0.0 0 32768 i
*> 10.16.0.0/24 169.254.83.193 100 0 16550 ?
*> 10.32.0.0/24 169.254.83.193 100 0 16550 ?
Ping started to work from spoke1 to on-prem router.
Summary
- Interconnect require Cloud Router
- VLAN attachment and Cloud Router are regional constructs and need to land on a VPC
- GCP Cloud Router is a route reflector, similar to Azure Route Server
- VPC peering requires both directions, each direction have option to enable import/export routes. The option of enable import/export gives gradual control than the VPC peering of AWS/Azure.
- Peered VPC prefixes doesn’t get advertised by Cloud Router to on-premise automatically. Cloud Router is capable of perform custom advertisement towards on-premise, with the choice to advertise prefixes in the VPC that the Cloud Router is landed on.
- Dynamic routes received via Cloud Router can be exported to directly peered VPC.
- On directly peered VPC, imported dynamic routes are not visible in directly peered VPC -> Routes, but visible on NIC -> Routes, or via peering -> imported routes.
- Dynamic routes are visible in Cloud Router -> BGP session details.

well described Jun, thx for this post